Bad Rabbit first appeared in October of 2017 targeting organizations in Russia, Ukraine and the U.S. with an attack that is basically a new and improved NotPetya ransomware. Ukrainian authorities attribute Bad Rabbit to Black Energy, the threat group they also believe was behind NotPetya. Many security experts believe Black Energy operates in the interest and under the direction of the Russian government. The attack didn't last for a long time, indicating the controllers shut it down themselves.
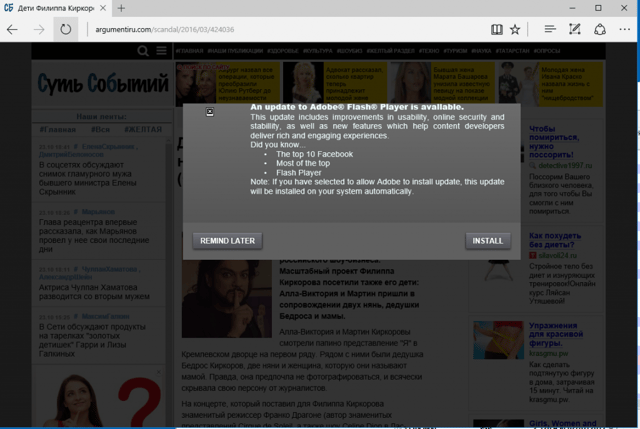
The attack started via files on hacked Russian media websites, using the popular social engineering trick of pretending to be an Adobe Flash installer. The ransomware demands a payment of 0.05 bitcoin, or about $275, giving victims 40 hours to pay before the ransom goes up.
This is basically NotPetya v2.0, with significant improvements over the earlier version. Bad Rabbit has many overlapping elements to the code of Petya/NotPetya, which so we can assume with a high degree of certainty that authors behind the attack are the same. They also tried to compose their malicious payload using stolen elements, however, the stolen Petya kernel has been substituted with a more advanced disk crypter in the form of a legitimate driver.
In this current campaign, encrypted data appears to be recoverable after paying the ransom, which means this BadRabbit attack is not as destructive as NotPetya. They fixed a lot of bugs in the file encryption process.
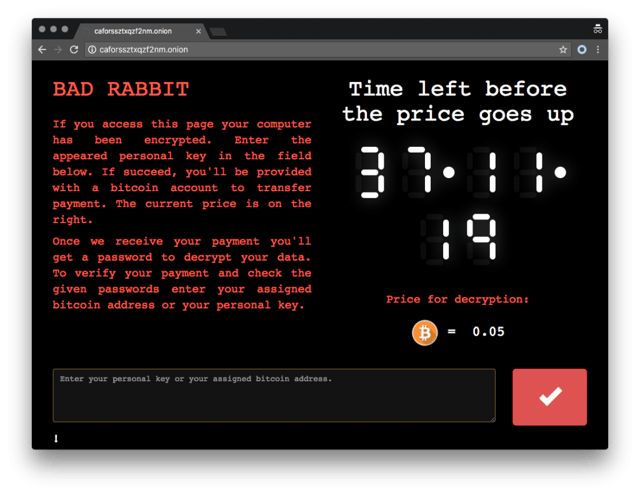
Bad Rabbit first encrypts files on the user's computer and then replaces the MBR (Master Boot Record). This means you need to buy two keys, one for the bootloader and one for the files themselves. This basically bricks the machine. More technical background at bleepingcomputer.
How to Inoculate a machine if your endpoint software does not block Bad Rabbit
Here are detailed instructions if you are in a hurry.
About a week after the initial attack Bad Rabbit was discovered to be a cover for a more insidious social engineering attack. Phishing campaigns targeted at a number of Ukrainian entities intended to compromise financial information and other sensitive data. Investigators believe that the perpetrator of Bad Rabbit and of the secondary phishing campaign are the same, with the goal of the secondary attack to gain undetected access well after the ransomware campaign stopped spreading.
“As cyber criminals get smarter and more sophisticated, it is important to remember that attacks are not always what they seem on the surface," Ben Johnson, co-founder and chief technology officer of Obsidian Security, told International Business Times. NotPetya also used ransomware as a cover for a secondary attack, and that's probably no coincidence.
