Chimera ransomware is distributed via malicious Dropbox links in phishing campaigns. When installed, it encrypts both local and network files. Chimera also attempts extortion on its victims.
Like most ransomware strains, it all starts with a spear phishing attack. This cyber-mafia sends email campaigns targeted at specific employees with job offers or business proposals with 'further information' in a link to a malicious payload hosted on Dropbox.
Once the Dropbox link is clicked, it triggers an automatic download of the trojan which immediately starts encrypting data on local and connected network drives. Encrypted files are then changed to the extension .crypt. After rebooting the computer and logging back on, the ransom note takes over the desktop. See screenshot below:
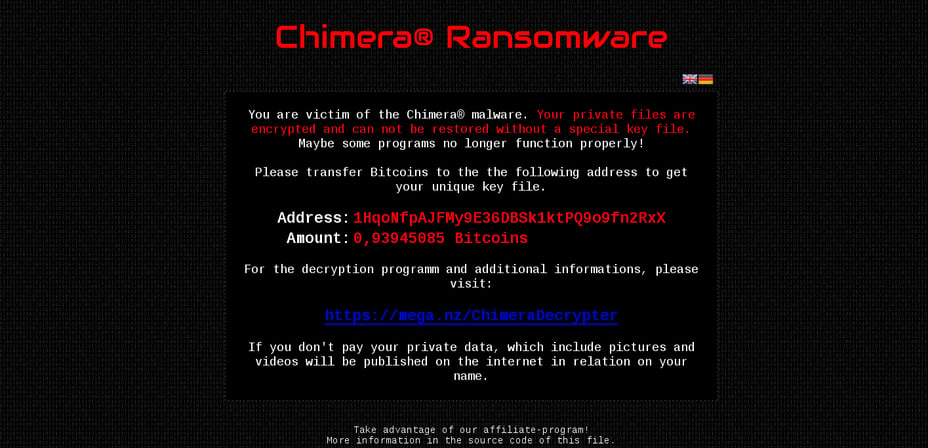
The criminals are asking for 2.5 Bitcoins, currently almost $1,000, to decrypt infected files. Here's the kicker: according to the note, Chimera's creators are threatening to make your files publicly available if the ransom is not paid. So even companies that do have solid backups may be tempted to pay because the possibility of sensitive information being published on the internet for all to see would cause much more damage than simply paying up. At this point it's unclear whether or not they are following through with the threat.
In addition to extortion, Chimera developers are apparently running an affiliate program and offering any takers 50% of the profits made:
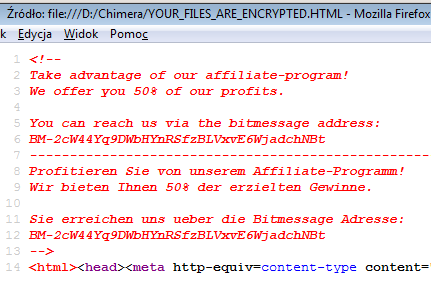
The good news is a free Chimera decryption now exists. If the first one doesn't work, try this alternative.
