Trend Micro reported a new ransomware that doesn’t encrypt files that are larger than 100MB and will skip anything in the C:\Windows, C:\Program Files and C:\Program Files (x86) folders. It uses AES rather than RSA encryption.
Let's first start off by saying that unlike other ransomware variants, CryptoBlocker will not make the rookie mistake of dropping any text files instructing the victim on how to decrypt their files. Instead, it gives victims this dialog box below. By entering a transaction ID in the text box, the victim will simultaneously trigger a message that states, “Transaction was sent and will be verified soon.”
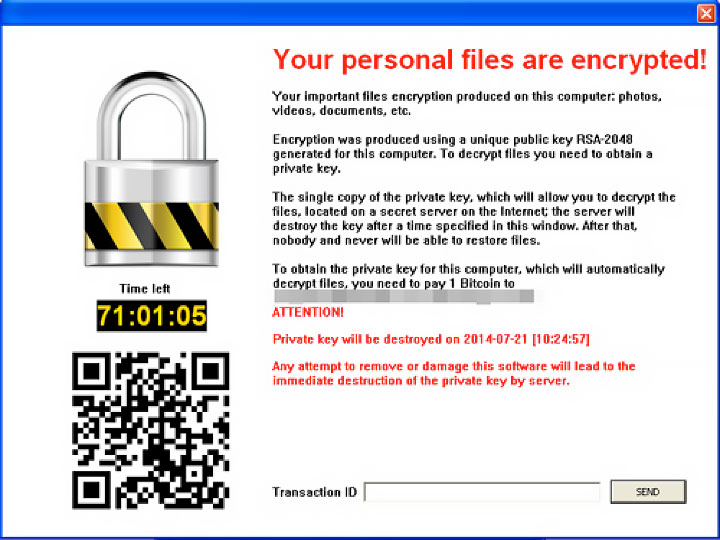
Another difference in this ransomware virus from its forefathers is its encryption routine. This malware does not use CryptoAPIs. CryptoAPIs are used to make RSA keys, which were not used with this particular malware. This is an interesting detail considering RSA keys would make decrypting files more difficult. It was found that the advanced encryption standard, also known as AES, is located in the malware code. This also very different from previous versions of the ransomware virus.
Upon further inspection, it was also revealed that the compiler notes were still intact upon unpacking the code. This is a distinctive detail because compiler notes are usually removed. The sole reason for this malware removal is because this information could be used against the malware writer by security researchers. This mistake let industry experts know that the creator of the CryptoBlocker virus was most likely a novice at best.
