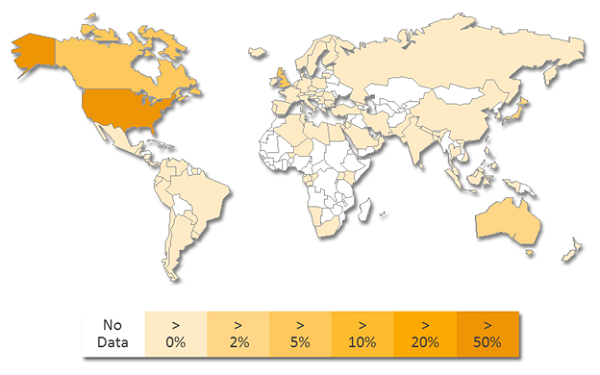
CryptoDefense ransomware used Tor and Bitcoin for anonymity and 2048-bit encryption. However, because it used Windows’ built-in encryption APIs, the private key was stored in plain text on the infected computer. Despite this flaw, the hackers still managed to earn at least $34,000 in the first month, according to Symantec. It was first discovered in February 2014, and largely targeted US and UK systems as you can see in the heatmap below.
CryptoDefense, like CryptoLocker, is spread via spear phishing email campaigns, and also claims to use RSA with 2048 bit keys to encrypt the user’s files. Much like CryptoLocker, CryptoDefense also makes claims that encrypted files are impossible to decrypted; but unlike CryptoLocker this claim was not totally true. There have only been about 11,000 infections and estimates that the operators were pulling in up to $38,000 a month in Bitcoin, based on data from BTC transaction sites.
The defining difference between CryptoDefense and CryptoLocker is that CryptoLocker produces its RSA key pair on the command and control server. While CryptoDefense, in its error, uses the Windows CryptoAPI to produce the key pair on the user’s system. For the novice computer user, this small distinction wouldn't make a world of difference, but to the well trained professional it is the tool needed to unlock the key that has been hidden. The poorly executed plan was a glaring problem that was produced by the think tank, that is the creators of CyrptoDefense, what they did not know was that the key to the unlock the infected users files was hidden in plain sight right on the user's systems. That just goes to show that not every ransomware cyber gang is a smart as they let on.
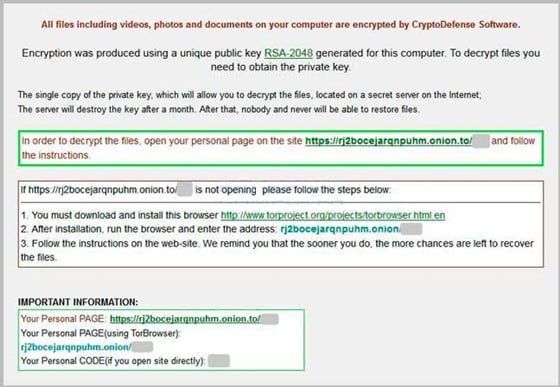
Luckily for the victims a rookie mistake was made and CryptoDefense was created for naught. You see, whoever coded the virus didn't know the important information that is detailed above and cost themselves a ton on ransom money. Thanks to the quick minds of some industry experts the entire ransomware strand didn't stand a chance. Here is Symantec’s explanation:
As advertised by the malware authors in the ransom demand, the files were encrypted with an RSA-2048 key generated on the victim’s computer. This was done using Microsoft’s own cryptographic infrastructure and Windows APIs to perform the key generation before sending it back in plain text to the attacker’s server. However, using this method means that the decryption key the attackers are holding for ransom, actually still remains on the infected computer after transmission to the attacker's server.
Infected users should check in the Application Data > Application Data > Microsoft > Crypto > RSA folder of their PCs for the private key.
