CryptoLocker 2.0 is the second version of CryptoLocker, a particularly nasty ransomware virus that had infected over 200,000 computer systems. CryptoLocker 2.0 uses 1024 bit RSA key pair uploaded to a command-and-control server, which it uses it to encrypt or lock files with certain extensions and delete the originals.
Once files are locked, Cryptolocker 2.0 then threatens to delete the private key needed to unlock the files if payment is not received within three days. Some experts believe that CyrptoLocker 2.0 is not an extension of the CryptoLocker ransomware, but, may, be a copycat. They speculate that the new strand is simply using CryptoLocker as a base.
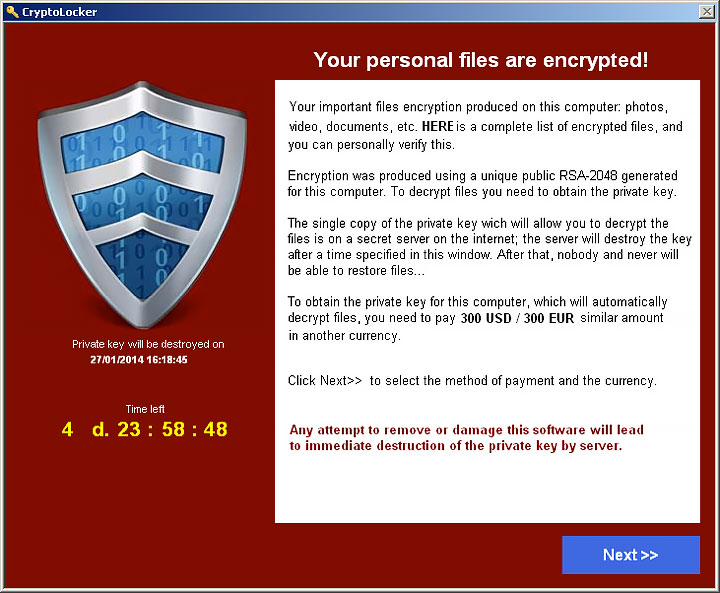
Cryptolocker 2.0 demands that payments be paid in the form of Bitcoins. If payments are not received in three days victims are usually given a second opportunity to pay a much higher ransom to get their files back. There isn't a person on earth that would want a virus on their computer, but there are particularly nasty ones that many dread. CyrptoLocker is one of them. The latest CryptoLocker is just as malicious as its predecessor if not worse.
Differences between CryptoLocker and CryptoLocker 2.0
Additionally CryptoLocker can now worm its way through USBs. This new innovation makes the bug portable and much easier to spread, thus increasing ransoms exponentially. It also poses as an updater for Adobe Photoshop and Microsoft Office on sites frequently used by P2P file sharers. Where the bad guys get the upper hand to these changes are: Using hard-coding to make it simpler to spread from P2P sites. This helps them keep a shroud of invisibility way and it eliminates the need for phishing emails. What also makes the CryptoLocker interesting is its ability to steal Bitcoin Wallets and its navigation into locking music and graphic files, meaning it is not only going after the big fish, but the smaller fish as well.
The only good news is that the original CryptoLocker is all but obsolete, thanks to the work of the FBI who took down its servers.
