CryptorBit is a ransomware virus that corrupts the first 212 or 1024 bytes of any data file it finds. CryptorBit is particularly nasty as it is able to bypass Group Policy settings put in place to defend against this type of ransomware infection.
CryptorBit infects PCs by using social engineering by getting people to install the virus by masquerading as legitimate antivirus software or updates for popular software titles like Adobe Flash. Once CryptorBit has encrypted the files, the user is asked to install the Tor Browser, enter their address and to follow the instructions to make the ransom payment – up to $500 in Bitcoin. CryptorBit also installs Cryptocoin mining software that uses the victim’s computer to gain access to personal digital coin accounts such and deposit the stolen funds into the malware developer’s digital wallet.
CryptorBit was first spotted on September 2013. Contrary to popular belief, it is not a variant of Cryptolocker but it does do most of the same things.
It is a virus that powers on when links are clicked within spear phishing emails, within websites, or by opening attachments in emails. And, just like CryptoLocker, once it has infected your systems, it will encrypt your files and hold them for digital ransom until it is paid or time runs out. The affected file types include Word files, Excel files, Pictures, Music, Movies, QuickBooks files, PDFs and all other data files on a computer system. Next, the Warning note on the screen then instructs the victim to download the Tor browser and access an onion-based hidden website to extort the monies. For those who don't pay the ransom, their files will be irreversibly damaged if the ransom is not paid on time.
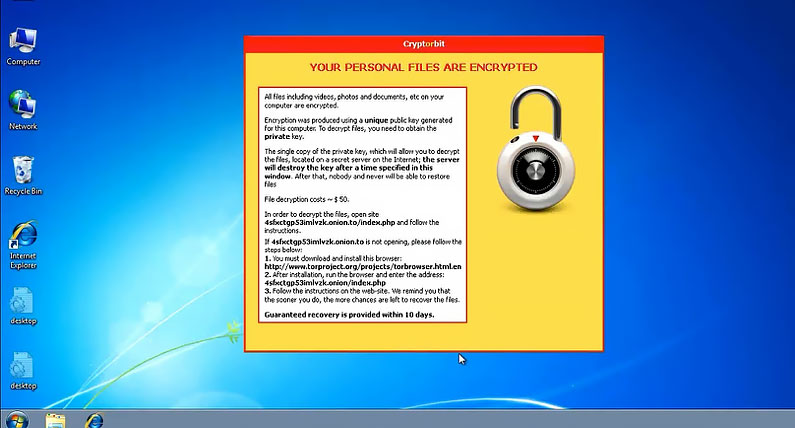
What's even scarier about this particular strand of ransom ware is that it is a complete scam. A growing number of victims have reported that although they paid the ransom, the cyber criminals did not decrypt their files leaving them with a paid balance but no results. That isn't even the tip of the iceberg the virus can also interfere with your privacy and leave lasting damage to your PC. According to Hacker News, the most common windows folder location where the Cryptorbit virus lives - "%AppData%" and can be easily removed using Antivirus tools; but unlike traditional Ransomware, you can decrypt your files using system utility 'System Restore'.
It is also important to note that these cyber criminals are crafty and will produce emails that look like they are from friends, coworkers and loved ones to get you to open them. Be sure to read the email carefully and always check the email address for any errors. The spam emails may appear to be sent from people you know, so it’s very important for users to be careful while reading such malicious emails and if it doesn’t look right, it’s probably not.
A new ransomware called KEYHolder was released by the CryptorBit gang in December 2014.
