Department of Homeland Security ransomware, also called Trojan Cbeplay.P, is similar in nature to Urausy Police ransomware. However, this particular ransomware is exclusive to the United States. Like the Urausy ransomware, the Homeland Security ransomware locks its victims’ computers, blocking access to files. It then sends the user a notice supposedly written by the U.S. Department of Homeland Security National Cyber Security Division.
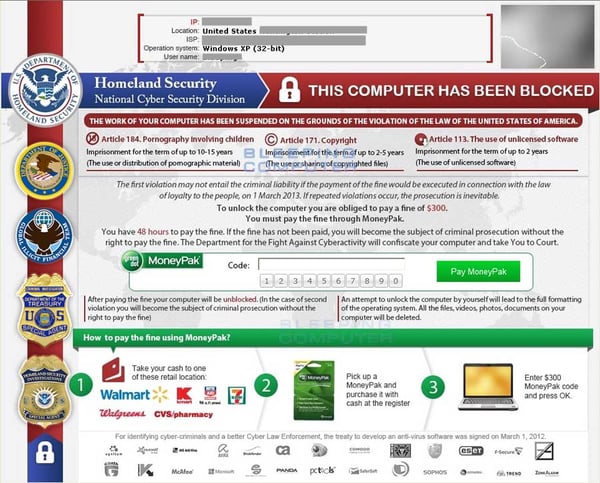
These notices accuse victims of such actions as piracy, illegally distributing copyrighted material or possessing and distributing child pornography. Like the U.S. version of Urausy ransomware, the Homeland Security ransomware demands a payment via MoneyPak voucher, usually of $300. If this payment is not made within 48 hours, then the victim’s computer will remain locked, claims the notice. To further frighten victims, the Homeland Security ransomware may also turn on the victim’s webcam, simulating that the Department of Homeland Security is monitoring the victim’s activity.
The Homeland Security ransomware may infect a user’s computer if he or she has visited a compromised or hacked website, or if he or she has received an email with an infected attachment. Like many other types of ransomware, Homeland Security ransomware obscures itself within the computer by installing itself without the user knowing about it. And then, once the victim restarts the infected computer, the notice supposedly from the Department of Homeland Security pops up and the computer’s files are blocked.
Anyone who happens to experience a Homeland Security malware infection must remember that the Department of Homeland Security would never block a person’s computer in this manner and that they would certainly not demand a $300 payment via MoneyPak like this.
