1980s
A phishing technique was described in detail in a paper and presentation delivered to the 1987 International HP Users Group, Interex.
More than 90% of successful hacks and data breaches start with phishing scams. Phishing is a threat to every organization across the globe. Get the information you need to prevent attacks.
Phishing is the process of attempting to acquire sensitive information such as usernames, passwords and credit card details by masquerading as a trustworthy entity using bulk email which tries to evade spam filters.
Emails claiming to be from popular social web sites, banks, auction sites, or IT administrators are commonly used to lure the unsuspecting public. It’s a form of criminally fraudulent social engineering.
A phishing technique was described in detail in a paper and presentation delivered to the 1987 International HP Users Group, Interex.
The first known mention of the term ‘phishing’ was in 1996 in the hacking tool AOHell by a well-known hacker and spammer.
Early Days
This is about the time phishing as we know it started, although the technique wasn't well-known to the average user until almost 10 years later. Phishing scams use spoofed emails, fake websites, etc. as a hook to get people to voluntarily hand over sensitive information. It makes sense that the term “phishing” is commonly used to describe these ploys. Hackers in the early days called themselves ‘phreaks’, referring to the exploration, experimenting and study of telecommunication systems. Phreaks and hackers have always been closely related, and the ‘ph’ spelling linked phishing attacks with these underground communities.
AOL Origins
In 1995, America Online (AOL) was the top internet service provider with millions of visitors logging in every day. Because it was so popular, it was targeted by phreaks and hackers with bad intentions. Since the beginning, hackers and those who traded pirated software used AOL and worked together, forming the warez community. It was this community that eventually made the first moves to conduct phishing attacks.
First Attempts
Phishing attempts started with hackers stealing user passwords and creating random credit card numbers. While lucky hits were few and far between, they made enough money to cause a lot of damage and to keep doing what they were doing. They would open bogus AOL accounts with the random credit card numbers and use those accounts to spam users. AOHell was a Windows application that made this process more automated, released in 1995. AOL put security measures to prevent this practice, shutting down AOHell later in the year.
Phishers then moved on to create a different type of phishing attack, using techniques we still see today. They started sending messages to users, claiming to be AOL employees using AOL’s instant messenger and email systems. A lot of people willingly ‘verified their accounts’ or handed over their billing information to the bad guys. This was an unprecedented attack so people didn’t know what to watch out for, they believed the requests were legitimate.
The problem got even worse when phishers set up AIM accounts to send their phishing messages; the accounts didn’t fall under AOL’s Terms of Service. Eventually, AOL added warnings on all email and instant messenger clients stating "no one working at AOL will ask for your password or billing information". Policy enforcement then forced copyright infringement of off AOL’s servers, and AOL deactivated all phishing accounts and shutting down the warez community.
In a lot of ways, phishing hasn’t changed much since early AOL attacks. In 2001, however, phishers began exploiting online payment systems. The first attack was on E-Gold in June 2001, and later in the year a "post-9/11 id check" was carried out soon after the September 11 attacks on the World Trade Center.
Beginnings of Email Phishing
In 2003, phishers registered dozens of domains that were very similar to eBay and PayPal, and could pass as their legitimate counterparts if you weren't paying close enough attention. Email worm programs sent phishing emails to PayPal customers (containing the fake website links), asking them to update their credit card numbers and other personally identifiable information. Also, the first known phishing attack against a bank was reported by The Banker in September 2003.
By early 2004, phishers were seeing major success for their exploits. It is estimated that between May 2004 and May 2005, approximately 1.2 million computer users in the United States suffered losses caused by phishing, totaling approximately US $929 million. United States businesses were losing about US $2 billion per year to phishing.
Phishers Go Pro
Phishing was officially recognized in 2004 as a fully organized part of the black market. Specialized software emerged on a global scale that could handle phishing payments, which in turn outsourced a huge risk. The software was then implemented into phishing campaigns by organized crime gangs.
Almost half of phishing thefts in 2006 were committed by groups operating through the Russian Business Network based in St. Petersburg. Customers disputed with their banks to recover phishing losses. The UK banking body APACS had the viewpoint that "customers must also take sensible precautions ... so that they are not vulnerable to the criminal." Similarly, when an initial flurry of phishing attacks hit the Irish Republic's banking sector in September 2006, the Bank of Ireland refused to cover customer losses at first, although losses to the tune of €113,000 were eventually made good.
Phishers continued to target customers of banks and online payment services, given early success. Emails claiming to be from the Internal Revenue Service have been used to capture sensitive data from U.S. taxpayers, which is still a popular ruse today. While the earliest examples were sent en masse with attackers hoping to get a few lucky strikes, it is reasonable to assume that phishers today can determine which banks their targets use and adjust their campaigns accordingly.
Social networking sites became a prime target of phishing, since the personal details freely shared on those sites can be used in identity theft. In late 2006 a computer worm unleashed on MySpace altered links to direct users to fake websites made to steal login credentials. Experiments have shown a success rate of more than 70% for phishing attacks on social networks.
A report from Gartner in 2007 claimed 3.6 million users lost $3.2 billion in a one year span. However, Microsoft claimed that number was exaggerated, dropping the annual phishing loss in the US to $60 million.
Attackers who broke into TD Ameritrade's database and took 6.3 million email addresses, but to do more damage they also needed account usernames and passwords. With the stolen email list they launched a follow-up spear phishing campaign.
The file sharing service RapidShare was targeted in 2008 by malicious actors who discovered they could open a premium account, thereby removing speed caps on downloads, auto-removal of uploads, waits on downloads, and cool down times between uploads. In a nutshell it made phishing campaigns much easier to execute.
Bitcoin and other cryptocurrencies were launched in late 2008, allowing transactions involving malicious software to be secure and anonymous.
In January 2009, a single phishing attack earned cybercriminals US $1.9 million in unauthorized wire transfers through Experi-Metal's online banking accounts.
At the end of 2009, the Anti-Phishing Working Group reported that they received over 115K reported phishing emails from consumers in the 3rd quarter alone, with the US and China hosting more than 25% of the phishing sites each.
In March 2011, Internal RSA staff were successfully phished, leading to the master keys for all RSA security tokens being stolen, which were used to break into US defense suppliers.
A Chinese phishing campaign targeted the Gmail accounts of senior officials of the United States and South Korean governments and militaries, as well as Chinese political activists. The Chinese government denied accusations that they were involved in the cyber-attacks, but there is evidence that the People’s Liberation Army has assisted in the coding of cyber-attack software.
In August 2013, advertising platform Outbrain became a victim of spear phishing when the Syrian Electronic Army placed redirects into the websites of The Washington Post, Time, and CNN.
In November 2013, Target suffered a data breach in which 110 million credit card records were stolen from customers, via a phished subcontractor account. Target’s CEO and IT security staff members were subsequently fired.
Between September and December of 2013, Cryptolocker ransomware infected 250,000 personal computers with two different phishing emails. The first had a Zip archive attachment that claimed to be a customer complaint and targeted businesses, the second contained a malicious link with a message regarding a problem clearing a check and targeted the general public. Cryptolocker scrambles and locks files on the computer and requests the owner make a payment in exchange for the key to unlock and decrypt the files. According to Dell SecureWorks, 0.4% or more of those infected paid criminals the ransom.
In January 2014, the Seculert Research Lab identified a new targeted attack that used Xtreme RAT (Remote Access Toolkit). Spear phishing emails targeted Israeli organizations to deploy the advanced malware. 15 machines were compromised - including those belonging to the Civil Administration of Judea and Samaria.
In August 2014, iCloud leaked almost 500 private celebrity photos, many containing nudity. It was discovered during the investigation that Ryan Collins accomplished this phishing attack by sending emails to the victims that looked like legitimate Apple and Google warnings, alerting the victims that their accounts may have been compromised and asking for their account details. The victims would enter their password, and Collins gained access to their accounts, downloading emails and iCloud backups.
In September 2014, Home Depot suffered a massive breach, with the personal and credit card data of 100+million shoppers posted for sale on hacking websites.
In November 2014, ICANN employees became victims of spear phishing attacks, and its DNS zone administration system was compromised, allowing the attackers to get zone files and personal data about users in the system, such as their real names, contact information, and salted hashes of their passwords. Using these stolen credentials, the hackers tunneled into ICANN's network and compromised the Centralized Zone Data System (CZDS), their Whois portal and more.
Former U.S. Nuclear Regulatory Commission Employee Charles H. Eccleston plead guilty to one count of attempted unauthorized access and intentional damage to a protected computer. His failed spear phishing cyber attack on January 15, 2015 was an attempt to infect the computers of 80 Department of Energy employees in hopes of receiving information he could then sell.
Members of Bellingcat, a group of journalists researching the shoot down of Malaysia Airlines Flight 17 over Ukraine, were targeted by several spear phishing emails. The messages were phony Gmail security notices containing Bit.ly and TinyCC shortened URLs. According to ThreatConnect, some of the phishing emails had originated from servers that Fancy Bear had used in other attacks previously. Bellingcat is best known for accusing Russia of being culpable for the shoot down of MH17, and is frequently ridiculed in the Russian media.
In August 2015, another sophisticated hacking group attributed to the Russian Federation, nicknamed Cozy Bear, was linked to a spear phishing attack against the Pentagon email system, shutting down the unclassified email system used by the Joint Chiefs of Staff office.
In August 2015, Fancy Bear used a zero-day exploit of Java, spoofing the Electronic Frontier Foundation and launched attacks against the White House and NATO. The hackers used a spear phishing attack, directing emails to the fraudulent url electronicfrontierfoundation.org.
Fancy Bear launched a spear phishing campaign against email addresses associated with the Democratic National Committee in the first quarter of 2016. The hackers were quiet on April 15, which in Russia happens to be a holiday honoring their military's electronic warfare services. Cozy Bear also had activity in the DNC's servers around the same time. The two groups seemed to be unaware of each other, as each separately stole the same passwords, essentially duplicating their efforts. Cozy Bear appears to be a separate agency more interested in traditional long-term espionage.
Fancy Bear is suspected to be behind a spear phishing attack on members of the Bundestag and other German political entities in August 2016. Authorities worried that sensitive information could be used by hackers to influence the public ahead of elections.
In August 2016, the World Anti-Doping Agency reported a phishing attack against their users, claiming to be official WADA communications requesting their login details. The registration and hosting information for the two domains provided by WADA pointed to Fancy Bear.
Within hours of the 2016 U.S. election results, Russian hackers sent emails containing corrupt zip files from spoofed Harvard University email addresses. Russians used phishing techniques to publish fake news stories targeted at American voters.
In 2017, 76% of organizations experienced phishing attacks. Nearly half of information security professionals surveyed said that the rate of attacks had increased since 2016.
A massive phishing scam tricked Google and Facebook accounting departments into wiring money – a total of over $100 million – to overseas bank accounts under the control of a hacker. He has since been arrested by the US Department of Justice.
In August 2017, Amazon customers experienced the Amazon Prime Day phishing attack, in which hackers sent out seemingly legitimate deals. When Amazon’s customers tried to purchase the ‘deals’, the transaction would not be completed, prompting the retailer’s customers to input data that could be compromised and stolen.
Between January-August 2017, 191 serious health care privacy security breaches were reported to the Office of Civil rights reporting site (OCR) as required by US federal law under its HIPAA Breach notification Rule. The law requires that the Secretary of HHS as well as patients be notified within 60 days. If a breach occurs that affects the privacy of 500 or more patients the local media must be informed in their state and the health care entity must post a description of the incident and remedies publicly.
Equifax publicly announced a disastrous data breach in September 2017, compromising the personal information of about 143 million U.S. consumers. Because a big credit bureau tracks so much confidential information like social security numbers, full names, addresses, birth dates, and even drivers licenses and credit card numbers for some, this is a phishing attack nightmare waiting to happen.
The September 2017 Webroot Quarterly Threat Trends Report showed that 1.385 million new, unique phishing sites are created each month. This report is based on threat intelligence data derived from the industry's most advanced machine learning techniques, ensuring it's both timely and accurate.
Potential attendees for the 2017 International Conference on Cyber Conflict were targeted by at least one decoy document designed to resemble a CyCon U.S. flier, but which includes malware that's been previously used by the Fancy Bear hacker group, aka APT28.
A Google study released in November 2017 found that phishing victims are 400 times more likely to have their account hijacked than a random Google user, a figure that falls to 10 times for victims of a data breach. Phishing is much more dangerous because they capture the same details that Google uses in its risk assessment when users login, such as victim's geolocation, secret questions, phone numbers, and device identifiers.
In November of 2017, Kazakhstan-born Canadian citizen Karim Baratov pleaded guilty to the massive 2014 Yahoo hack that affected three billion accounts and admitted to helping the Russian intelligence.
PhishLabs published new analysis in December 2017 showing that phishers have been adopting HTTPS more and more often on their sites. When you get a phishing email or text, the sites they lead to—that try to trick you into entering credentials, personal information, and so on—implement web encryption about 24 percent of the time now, PhishLabs found. That's up from less than three percent at the same time last year, and less than one percent two years ago." The green padlock gives consumers a false sense of security. All it really does is indicate that traffic between the server and the user's browser is encrypted and protected against interception. Don't assume that any page that has HTTPS contains legitimate and authentic content!
Wombat Security Technologies' annual State of the Phish research report found that 76% of organizations experienced phishing attacks in 2017. There was an 80% increase in reports of malware infections, account compromise and data loss related to phishing attacks over 2016. The data also revealed smishing (SMS/text message phishing) as an emerging threat: 45% of infosec professionals reported experiencing phishing via phone calls (vishing) and smishing.
Cryptomining overtook ransomware as a tool of choice for extorting money online in December 2017 according to Check Point's Global Threat Index. Phishing is unsurprisingly the most used infection vector for this type of attack.
In December 2017, production of AI-assisted fake porn has “exploded,” reported Motherboard. Thousands of people are doing it, and the results are ever more difficult to spot as fakes. Cybercriminals will have a field day with this technology and attempt to manipulate innocent people and shock them to click on a video link in a phishing email in order to prevent possibly very negative consequences if co-workers, friends and family might "find out, or might see".
A phishing campaign targeting organizations associated with the 2018 Winter Olympics was the first to use PowerShell tool called Invoke-PSImage that allows attackers to hide malicious scripts in the pixels of otherwise benign-looking image files, and later execute them directly from memory. Not only does hiding the script inside an image file help it evade detection, executing it directly from memory is a fileless technique that generally won't get picked up by traditional antivirus solutions. This attack is another troubling example of how attacks are evolving away from using malicious .exe's.
A trend In phishing called conversation hijacking was seen in February 2018. With this new technique, hackers insert themselves into email conversations between parties known to and trusted by one another. Once in, they exploit that trust to trick users to launch an executable. Variations of this scheme are very difficult to detect and beat.
Under Armour's health and fitness-tracking app, MyFitnessPal, was hit by a data breach in March of 2018. According to the company the breach affected roughly 150 million users, making them all phishing targets.
Later in March of 2018, researchers at Check Point and CyberInt discovered a new generation of phishing kit readily available on the Dark Web to cybercriminals. The kit enables users to craft convincing emails and redirect sites that closely mimic branding elements of well-known firms and launch a phishing campaign that collects the personal and financial information of unsuspecting consumers, very quickly.
The notorious Necurs botnet adopted a retro trick to make itself more evasive and less likely to have its phishing intercepted by traditional av filters. The emails have an archive file attachment made to look like a voice mail message you have missed.
A white hat hacker developed an exploit that breaks LinkedIn 2-factor authentication and was published on GitHub in May of 2018. See the video that shows how the exploit is based on a credentials phishing attack that uses a typo-squatting domain.
According to a federal court decision, an employee who is tricked into sharing personal information in response to a phishing email can be seen as committing an intentional disclosure under the North Carolina Identity Theft Protection Act (NCITPA). Global manufacturing firm Schletter, Inc. found out the hard way in a class-action suit filed after an employee of the organization fell victim to a CEO Fraud W-2 phishing email. The court reasoned that the data disclosure was intentional and therefore allowed the employees filing the lawsuit to seek treble damages from Schletter.
Marketing firm Exactis leaked a database with 340 million personal data records in June of 2018. Close to two terabytes of data goes into minute detail for each individual listed, including phone numbers, home addresses, email addresses, and other highly personal characteristics for every name.
Cybercriminals are using internationalized domain names (IDN) to register domain names with characters other than Basic Latin. For every 1 top global brand, threat intelligence vendor Farsight Security found nearly 20 fake domains registered, with 91% of them offering some kind of web page. Phishing emails containing these domains are very convincing and hard to detect.
Payroll phishing is always a tax season favorite for cybercriminals, but new campaigns are seen year round with a request to HR for C-level employee pay stubs and wage statements.
A sextortion phishing campaign seen in July 2018 was the first to use recipient's actual hacked passwords in the emails to convince people that the hacking threat is real. Given the sheer volume of hacked and stolen personal data now available online, this is a big threat to watch out for in 2018.
A Lookout report published in July of 2018 showed that the rate at which users are falling victim to mobile phishing attacks has increased 85% every year since 2011, and that 25% of employees click on links found in text messages. Facebook messenger is another medium used.
Massive SharePoint phishing attack on Office 365 users links to SharePoint Online-based URLS, which adds credibility and legitimacy to the email and link. Users are then shown a OneDrive prompt with an "Access Document" hyperlink that is actually a malicious URL that if clicked, brings them to an Office 365 logon screen where the cybercriminals harvest the user’s credentials.
The Turla threat group, certainly Russian-speaking and widely attributed to Russian intelligence services, started using a new phishing technique in August 2018. The threat actor is distributing emails whose payloads, malicious pdf files, install a stealthy backdoor and exfiltrate data via email.
Researchers at FireEye examined over half-a-billion emails sent between January and June 2018 and found that one in 101 emails are classed as outright malicious, sent with the goal of compromising a user or network.
The Anti-Phishing Working Group's (APWG) Q1 2018 phishing trends report highlights: Over 11,000 phishing domains were created in Q1, the total number of phishing sites increased 46% over Q4 2017 and the use of SSL certificates on phishing sites continues to increase to lull visitors into a false sense of security and site legitimacy.
Trustwave, a provider of ethical hacking services, released Social Mapper in August 2018 – it's a tool that uses facial recognition to identify associated social media accounts for an individual. While Trustwave is using this technology to improve the security of their customers, they point out how facial recognition could be used by cybercriminals to improve the accuracy and effectiveness of phishing scams. Examples include using actual profile pictures in phishing emails, creating fake social media profiles, and doxing potential victim’s social media accounts.
According to RSA’s Quarterly Fraud Report: Q2 2018, 41% of successful online, e-commerce and mobile fraud attacks are enabled by phishing scams. Cybercriminals leveraging phishing scams to obtain banking credentials, credit card details, and even control over mobile devices in an effort to commit fraud.
The GRU, the Russian military intelligence spy agency which was responsible for the 2016 election cyber attacks, began targeting the U.S. Senate and conservative groups in August 2018 prior to midterm elections. Microsoft took down six internet domains spoofing legitimate websites, which marked the early stages of spear-phishing attacks intended to compromise political operatives working for or around the targeted organizations.
The Turla threat group, widely attributed to Russian intelligence services, is back with a new phishing technique. The threat actor is distributing emails whose payloads, malicious pdf files, install a stealthy backdoor. To date, it's the only known case of malware that's completely controllable via email.
In August of 2018 Google reiterated its warnings of phishing attacks coming from a few dozen foreign governments. Google’s concern revolves around governments attempting to con users out of their Google password – giving them access to countless services including email, the G Suite, cloud-based file data, and more.
A mobile phishing campaign reported in August 2018 involved an internationalized domain name (IDN) "homograph-based" phishing website that tricked mobile users into inputting their personal information. The websites presented as commercial airline carriers and offered free tickets, fooling users with the age-old bait-and-switch technique.
Only 40% of business phishing scams contain links, according to a recently released report from Barracuda Networks in which the security vendor analyzed over 3,000 Business Email Compromise (BEC) attacks. These attacks leverage company email purporting to be someone within the organization, and have one of four objectives in mind: Establish rapport, Get the recipient to click a malicious link, Steal personally identifiable information or Obtain a Wire Transfer.
Cybercriminals are no longer resorting to shotgun blast-type mass attacks in the hopes someone will fall victim; they are doing their homework, choosing victims, coming up with targeted and contextual campaigns, and executing their plans. And, from the looks of the data found in ProofPoint’s September 2018 report, Protecting People: A Quarterly Analysis of Highly Targeted Attacks, the cybercriminals are stepping up their game. Malicious email volume rose 35% over last quarter, Targeted companies experienced 25% more email fraud attacks than last quarter, and 85% more than the same quarter last year.
A new academic study published in September 2018 reveals that Android-based password managers have a hard time distinguishing between legitimate and fake applications, leading to easy phishing scenarios. Android versions of Keeper, Dashlane, LastPass, and 1Password were found to be vulnerable and have prompted the user to autofill credentials on fake apps during tests. Researchers found that Google's Smart Lock app did not fall for this fake package name trick, and the reason was because it used a system named Digital Asset Links to authenticate and connect apps to a particular online service.
KnowBe4 released Domain Doppelgänger in September of 2018. This free tool identifies the look-alike domains associated with your corporate domain. These are a dangerous vector for phishing and other social engineering attacks, so you want to know if any potentially harmful domains can spoof your domain.
In October of 2018 we saw the growth of a cleverly crafted phishing campaign aimed at employees of public school districts and small colleges, including community colleges. In this campaign the bad guys flood educational organizations with emails purporting to be from a senior figure. These malicious emails typically announce new policies governing employee conduct or a renewed focus in the organization on proper, ethical professional behavior. These malicious emails deliver attachments -- both Word docs and PDF documents that require users to click through to slickly designed external web pages inviting them to cough up their login credentials.
A malicious group known as the “Inception” attackers has been using a year-old Office exploit and a new backdoor in recent attacks. Active since at least 2014, the group has used custom malware and against targets spanning various industries worldwide, with a special interest in Russia. In October 2018, the threat actor was observed hitting various European targets in attacks employing an exploit for a vulnerability (CVE-2017-11882) that Microsoft patched in November 2017. Furthermore, the hackers were using a new PowerShell backdoor dubbed POWERSHOWER, which revealed high attention to detail in terms of cleaning up after infection.
Microsoft recently announced a big update to their Microsoft Office 365 (O365) anti-phishing technical capabilities. According to Microsoft, their “miss phish catch rate” is down to near zero, beating all other O365 anti-phish competitors by orders of magnitude.
RSA’s Q3 Fraud Report released in November of 2018 shows a 70% rise in phishing attack volume making phishing the number 1 attack method for financial fraud attacks. This increase highlights the simplicity and effectiveness of phishing (via email, phone call or SMS text, according to the report). The work necessary to fool an individual – given the ability for attackers to hit millions of email recipients at once – is minimal when compared to the financial take on the other end of the scam.
Russian banks were being targeted by sophisticated phishing emails in November 2018, something that doesn't happen too often. The phishing emails purported to come from the Central Bank of Russia (CBR), according to a report by Group-IB. The emails contained malicious attachments that delivered a tool used by the Silence hacker group and were nearly identical to official CBR correspondence. Fortunately, the emails did not pass DKIM validation, so their effectiveness was somewhat stunted. A month earlier, another group known as “MoneyTaker” targeted Russian banks with phishing emails supposedly from Russia’s Financial Sector Computer Emergency Response Team (FinCERT). These emails also contained attachments that imitated official CBR documents and triggered a download for the Meterpreter Stager.
Data from PhishLabs shows that 49% of all phishing sites in third quarter 2018 had the padlock icon many users look for as a sign of a secure and legitimate website. This is up 25% from a year ago. Since a majority of users take “look for the lock” to heart, this new finding is significant. 80% of the respondents to a PhishLabs survey believed the lock indicated a safe website.
One of the distribution models for ransomware that is gaining popularity is the use of an affiliate network of attackers. The creators of the latest iteration of this model, FilesLocker, are looking for affiliate organizations and individuals with proven track records of distributing ransomware via phishing, social engineering, or other methods, specifying that affiliates must meet an infection minimum of 10 per day. Affiliates can expect anywhere from 60-75% of the ransoms generated through their actions.
Kaspersky Lab blocked 137 million phishing attempts in the third quarter of 2018, a 28 percent increase compared to Q2 2018. A report by the anti-virus company reveals that phishing attacks targeted 12% of Kaspersky’s customers around the world. More than a third of the attacks were directed at financial targets, including banks, electronic payment systems, and online stores. The report’s findings are consistent with a global increase in phishing over the past several years. Kaspersky Lab’s anti-phishing system blocked 154 million phishing attempts in 2016 and 246 million attempts in 2017. Both numbers have already been far surpassed in the first three quarters of 2018, with this year’s prevented attacks reaching well over 300 million.
The National Republican Congressional Committee (NRCC) was hacked during the 2018 midterm elections, according to a report from Politico. Republican officials said that hackers had access to four senior NRCC aides’ email accounts for “several months,” until a security firm discovered the intrusion in April. The NRCC launched an internal investigation and alerted the FBI, but it did not inform any Republican legislators until this week.
Researchers discovered over 1,150 new HTTPS phishing sites over the course of one day, not including the plethora of the malicious HTTP phishing URLs that we already know exist meaning a new secure phishing site goes up every two minutes. "Seeing a padlock in the URL bar used to be a reliable safety check but because the vast majority of websites now use encryption, hackers are also ‘securing’ their sites to lure victims into a false sense of security,” researchers said in a SC Media exclusive. “These days, there is no real barrier to entry for getting an SSL certificate, which means it’s incredibly simple for hackers to obtain them while keeping their tracks covered. Some certificate issuers are even offering SSL certificates without requiring payments or genuine personal identifiable information needing to exchange hands. Threat actors are also using domain control validation, in which only the control of the subject has been verified, to hide their identity."
In January of 2019, researchers at Proofpoint discovered a phishing template that uses a unique method for encoding text using web fonts. They found that the source code of the landing page contained encoded text, but the browser unexpectedly renders it as cleartext.
A three-year-long cyber-attack led to the successful breach of all communications between all EU member states in January 2019, putting countries and their futures at risk. The EU’s diplomatic network is a secure means by which member states can exchange some of the world’s most sensitive information – literally having impacts on a geopolitical scale. A report by antiphishing vendor Area 1 Security highlights the attack targeting this network, attributing it to the Strategic Support Force (SSF) of the People’s Liberation Army (PLA) of China.
Phishing campaigns during the partial U.S. government shut down in January 2019 caused widespread confusion over whether the IRS will be sufficiently operational to process tax returns and issue refunds. First, amidst a more general increase in vishing, users' inboxes were flooded with ominous warnings about alleged voice mails from the IRS. Second, as in previous years malicious actors were targeting accounting firms and legal practices that specialize in tax matters, pretending to be new clients looking for help with tax preparation and related issues. While the goal of these phishing emails is often to draw targeted employees into a back-and-forth that provides a pretext for malicious actors to hit potential marks with malicious Office documents that often install sophisticated backdoor trojans, in some cases the bad guys do not wait, offering up malicious links and attachments in the initial email.
Phishing is moving beyond the Inbox to your online experience in an effort to collect personal details and share out the attack on social networks, according to a new report from Akamai Enterprise Threat Research. According to Akamai, phishing campaigns like these “outperform” traditional campaigns with higher victim counts due to the social sharing aspect (which makes it feel like your friend on social media endorses the quiz, etc). These are currently focused on the consumer, but it’s not a stretch of the imagination to see this targeting business email.
According to Cybersecurity Ventures’ 2019 Official Annual Cybercrime Report released in January 2019, we should expect to see Ransomware attacks step up in frequency and cost. In 2016, Kaspersky Labs estimated the frequency of ransomware attacks to occur once every 40 seconds. Cybersecurity Ventures predicts this will rise to once every 14 seconds in 2019. In addition, the total cost of ransomware attacks is rising as well. According to the report, the total cost of ransomware in 2018 is estimated to be $8 billion, and will rise in 2019 to over $11.5 billion.
Proofpoint’s 2019 State of the Phish report shows that organizations are feeling the heat of phishing like never before – and feeling its’ impact as well. According to the report, all types of phishing attacks in 2018 occurred more frequently than in 2017. 96% of organizations said the rate of phishing attacks either increased or stayed consistent throughout the year, IT professionals experiencing spear phishing jumped nearly 21%, USB-based Social Engineering attacks experienced jumped 25%, Vishing and smishing increased by 9% and that's just the tip of the iceberg.
On Jan. 22, 2019, the Cybersecurity and Infrastructure Security Agency (CISA), which is a part of the U.S. Department of Homeland Security (DHS), issued Emergency Directive 19-01 titled Mitigate DNS Infrastructure Tampering. A series of actions are required for federal agencies, and here is the background:To address the significant and imminent risks to agency information and information systems presented by hacker activity, this emergency directive requires the following near-term actions to mitigate risks from undiscovered tampering, enable agencies to prevent illegitimate DNS activity for their domains, and detect unauthorized certificates
Gift card phishing campaigns have been growing since 2018 and the bad guys are actively adapting and evolving their pitch. They are getting much better at establishing a credible pretext (ie "incentives" for staff), explicitly request confidentiality, they're getting really greedy -- $4000 total in gift cards, the largest request we've yet seen, and they are incentivizing the entire scheme by offering the recipient a bribe ("take one for yourself"), a ploy which, in a way, seeks to turn the email recipient into a co-conspirator.
Cyren came out with a new report in Jan 2019 where they summarized a 2-year Email Security Gap Analysis study. They engaged with a diverse set of organizations through its program to assess the effectiveness of their current, live email security infrastructures. This report summarizes the results from a cross-section of 15 such engagements conducted in 2018, in which Cyren examined 2.7 million emails that were classified as clean by their existing email security systems and delivered to user mailboxes. Every email was also copied to Cyren for analysis. Of this total, 7.2% were found to be spam, phishing and malware.
A devilishly ingenious vishing scam seen in February 2019 plays on your user’s familiarity with business voicemail, seeking to compromise online credentials without raising concerns. Many organizations have their PBX system integrated with email; miss a call and the recording pops into your Inbox. Nothing inappropriate with this scenario. But, that’s exactly what scammers are hoping you’ll think when your users receive their email pretending to be an internal voicemail notification. Using subjects such as Voice:Message, Voice Delivery Report, or PBX Message, these emails contain another email as the attachment (to avoid detection by email scanning security solutions) containing the actual phish.
Sextortion scam emails continue to circulate which claim that a popular adult site has been hacked, allowing an attacker to record videos of users through their webcams. The attacker claims that these videos will be sent to all of the victim’s contacts unless the victim pays around $969 in Bitcoin. Some of the emails contain links, supposedly leading to sample videos of the victim as proof of the attacker’s claims.
Criminals are still using hijacked GoDaddy domains to launch spam campaigns, despite GoDaddy taking steps to address the authentication flaw exploited by the attackers. The spammers had realized that they could add domains to their GoDaddy accounts without proving that they owned the domains. A large-scale campaign using the hijacked domains to distribute phishing emails laden with GandCrab ransomware was observed in February of 2019.
A new phishing scam uses Google Translate to hide a spoofed logon page when asking a user for their Google credentials. The user is sent a supposed Google Security Alert about a new device accessing their Google account with a “Consult the Activity” button to find out more. The user is then taken to a spoofed Google logon page. The cybercriminals use Google Translate to display the page, filling up the URL bar and obfuscating the malicious domain.
As the story broke about the charges against former U.S. Air Force intelligence specialist who defected to Iran and support targeted hacking against some of her former colleagues, one clear takeaway stood out: even U.S. intelligence officers can fall victim to basic phishing schemes.
According to Danny Palmer at ZDNet: "A cyber espionage campaign is targeting national security think tanks and academic institutions in the US in what's believed to be an intelligence gathering operation by a hacking group working out of North Korea. A series of spear-phishing attacks using fake emails with malicious attachments attempts to deliver a new family of malware, dubbed BabyShark. The campaign started in November and remained active at least into the new year.
New 'NoRelationship' attack bypasses Office 365 email attachment security by editing the relationship files that are included with Office documents. A relationship file is an XML file that contains a list of essential components in the document, such as font tables, settings, and external links. A number of popular email filters only scan the links contained in the relationship file, rather than scanning the entire document. Attackers can remove the links from a document’s relationship file, but they will still be active in the actual document. Avanan has the full story.
A phishing campaign is using a phony Google reCAPTCHA system to deliver banking malware was observed in February 2019 by researchers at Sucuri. The attackers are sending emails, supposedly from a Polish bank, telling users to confirm an unknown transaction. Recipients that click the link get to a spoofed 404 error page. PHP code then replicates a reCAPTCHA using HTML and JavaScript to trick victims into thinking the site is real. The PHP code then either downloads a .zip dropper or an .apk file, depending on which device the victim is using.
Scams seeking to harvest online credentials have long tried to replicate known logon pages. But this newly found instance is just about perfect. Researchers at security vendor Myki found a website purporting to use Facebook for sign-on, but are instead providing an exact HTML copy of the logon page.
A growing percentage of cyberattacks are using encryption to avoid detection, according to a March 2019 report by Zscaler’s ThreatLabZ researchers. Last year, Zscaler’s platform detected and blocked 2.7 million encrypted phishing attacks per month. It also found that 32% of newly-registered, potentially malicious domains were using SSL certificates. In total, Zscaler blocked 1.7 billion attacks executed over SSL between July and December of 2018.
New details from international security company Group-IB’s Computer Forensic Lab shows how cybercriminals are no longer looking to just steal from one bank. Instead they chain their phishing attacks to improve their chances of success. One of the reasons, according to the report, is that Russian banks are easy targets: 74% of banks weren’t ready for an attack, 80% have no logging depth to investigate an attack and 70% have insufficient staff to investigate infections or attacks.
Microsoft’s latest Security Intelligence Report highlights the trends seen in 2018 with phishing as the preferred attack method and supply chains as a primary attack target. Microsoft saw a 250% rise in phishing attacks over the course of 2018, delivering malicious zero-day payloads to users. Microsoft admits that this rise has caused them to work to “harden against these attacks” signaling the attacks are becoming more sophisticated, evasive, and effective.
A December 2018 report from antivirus firm McAfee, a new campaign dubbed “Operation Sharpshooter” is showing signs of going global, demonstrating a concerted effort to hit organizations in industries including nuclear, defense, energy and financial groups. malicious source code is implanted into endpoints using a phishing attack disguised as legitimate industry job recruitment activity. The malicious code, 'Rising Sun' has source code that links it back to the Lazarus Group – a cybercriminal organization believed to be based out of North Korea that was responsible for the 2014 cyberattack against Sony Pictures Entertainment.
The latest report from the Anti-Phishing Working Group (APWG) 3rd Quarter Phishing Activity Trends Report highlights the prevalence of phishing and how it’s changing to remain an effective attack method. Highlights this quarter include: Unique phishing reports has remained steady from Q2 to Q3 of 2019, Payment processing firms remained the most-targeted companies, Phishing attacks hosted on secure sites continues its steady increase since 2015 and phishing attacks are using redirectors both prior to the phishing site landing page and following the submission of credentials to obfuscate detection via web server log referrer field monitoring. So how can organizations protect themselves? Expect phishing to continue and ensure all layers of protection, including security awareness training for users, is in place.
Three Romanian citizens have pleaded guilty to carrying out vishing and smishing schemes worth $21 million that used recorded messages and cellphone texts to trick thousands of people into revealing their social security numbers and bank account information, federal authorities said. The men stored the stolen PII on the compromised computers. The pilfered data was accessed by two of the suspects who then sold or used the information with the help of the third participant.
A new phishing campaign in March of 2019 spreads malware through emails that claim to have Bitcoin investment updates, according to My Online Security. The emails direct the victim to download an attachment, which is an [.]iso file with a fake file extension. The malware is thought to be a new Bitcoin currency stealer, although it’s difficult to tell exactly what it does because it appears to have anti-analysis capabilities.
Microsoft took control of 99 phishing domains operated by Iranian state hackers. The domains had been used as part of spear phishing campaigns aimed at users in the US and across the world. Court documents unsealed in March 2019 revealed that Microsoft has been waging a secret battle against a group of Iranian government-sponsored hackers. The OS maker sued and won a restraining order that allowed it to take control of 99 web domains that had been previously owned and operated by a group of Iranian hackers known in cyber-security circles as APT35, Phosphorus, Charming Kitten, and the Ajax Security Team.
Lower-level employees are the workers most likely to face highly-targeted attacks, according to the online marketing firm Reboot. Citing information from Proofpoint’s most recent quarterly analysis of highly-targeted cyberattacks, Reboot says that 67% of these attacks are launched against low-ranking employees. Contributors come in second, experiencing 40% of targeted attacks. Management and upper management both face 27% of these attacks.
Businesses and consumers see more than 1.2 million phishing attacks each year, as hackers use the effective social engineering attacks to con employees into clicking a malicious link or attachment. Despite how widely known and damaging these attacks can be, companies still fail to adequately prevent them from happening, according to a June report from Valimail. Furthermore, the vast majority—90%—of large tech companies remain unprotected from impersonation (CEO Fraud) attacks, the report found.
A new strain of the notorious Dridex malware has been spotted using polymorphism antivirus evasion techniques in phishing emails. The Dridex credential-stealer that almost exclusively targets financial institutions continues to evolve and now uses application whitelisting techniques to infect systems and evade most antivirus products.
A new phishing attack spotted by security researchers at PhishLabs uses a malicious Office 365 App rather than the traditional spoofed logon page to gain access to a user’s mailbox. Using traditional phishing tactics, victims are lured into clicking on a malicious link that appears to be hosted in SharePoint Online or in OneDrive. The malicious payload is a URL link that requests access to a user’s Office 365 mailbox: By pressing ‘Accept’, the bad guys are granted full access to the user’s mailbox and contacts, as well as any OneDrive files the user can access. Because the result of this attack is an app has been connected and granted access to an Office 365 account, resetting the user’s password has no effect. To eliminate the malicious access, the app must be disconnected – a completely separate process!
According to Microsoft, here are some of the innovative ways they’ve seen phishing attacks evolve from 2019 to 2020: Pointing email links to fake google search results that point to attacker-controlled malware-laden websites, pointing email links to non-existent pages on an attacker-controlled website so that a custom 404 page is presented that can be used to spoof logon pages for legitimate sites, spoofing company-specific Office 365 sign-in pages to look so realistic that users would give the logon page a second thought. These advancements in the way attackers are thinking about phishing to facilitate endpoint infection or credential theft make it necessary for organizations to no longer consider their security solutions as their only line of defense.
A vendor email compromise attack targeted the Special Olympics of New York, leverage their email system to reach their approximately 67K registered families with an adult or child having an intellectual disability. Their email server was apparently hacked in December and was used to send out phishing emails to their donors under the guise that a donation of nearly $2,000 was about to be posted automatically (creating the necessary sense of urgency on the part of the potential victim). Upon realizing the email had been sent out, a follow-up email was sent, communicating that Special Olympics New York was aware of the hack, that donors should ignore the email, and that no information – other than contact details – was accessed.
The Central Bank of Malta has issued a statement warning people about a bitcoin phishing scam being pushed by a spoofed news website, the Times of Malta reports. The site imitated a legitimate news outlet and attributed fake quotes to real people. The bank didn’t provide many details about the scam, but it presumably involved using social engineering to trick people into transferring bitcoin to a fraudulent account.
The latest cyber attack trend data in the U.K. shows the majority of data breaches in 2019 began with a phishing attack. Security consulting firm CybSafe analyzed three years of the U.K.’s Information Commissioner’s Office (ICO) cyber breach data from 2017 – 2019. The data was released in January 2020. Out of nearly 2400 reported data breaches, over 1000 – 45.5 percent – of attacks were initiated by a phishing attack.
The sophisticated 16Shop phishing kit can now target PayPal and American Express users, according to researchers from ZeroFOX. The researchers came across a new version of 16Shop that includes a PayPal kit designed to steal a wide variety of financial and personal information from users who speak English, Japanese, Spanish, German and Thai. The kit’s product page also reveals the existence of a brand new “Amex Scampage.”
Motherboard reports that SIM swappers are launching phishing attacks against employees at Verizon, T-Mobile, and Sprint in order to hijack customer service tools. Once they have access to these tools, the hackers can take over phone numbers directly without having to trick an employee into performing each swap for them. The attackers are using phishing pages that spoof the login portals of VPNs that the companies use to access these tools.
Yup, you can count on it, when there is a worldwide health scare, the bad guys are on it like flies on $#!+. We saw a new malicious phishing campaign in January 2020 that is based on the fear of the Coronavirus, and it's the first of many. The message is obviously not from the CDC and at the time of this writing, there are very very few local cases in America. Let's hope it stays that way.
A new slew of phishing attacks targeting victims interested in Oscar-nominated movies steals credit cards and installs malware. According to the researchers at Kaspersky, over 20 movie-related phishing sites have been identified with over 900 malicious files being offered up as movie downloads. Movies such as Joker, 1917, The Irishman, and Once Upon a Time in Hollywood are top searched movies used by scammers. Leveraging social media and presenting an offer to watch the movie, users are taken for a ride that includes surveys, providing personal details, and collecting credit card information.
New phishing campaign have been spotted that use Google Firebase Storage to get through email security filters. The phishing emails themselves are easy enough to spot, but the use of Firebase URLs means there is a much larger volume of phishing emails reaching users' inboxes.
Nearly all phishing emails and internet scams involve some type of malicious URL. Roger A. Grimes, KnowBe4's Data-Driven Defense Evangelist has outlined the most common types, and defenses against them, These include Look-alike Domains, Domain Mismatches, URL Shortening, URL Character Encoding, and much much more.
Scammers have been observed abusing a Google Drive feature to send phishing links in automated email notifications from Google. By mentioning a Google user in a Drive document, the scammers can cause Google to generate a notification that looks legitimate and will be sent straight to the user’s inbox, bypassing spam filters.
Phishing attacks using PDF files have spiked over the past year, according to researchers at Palo Alto Networks’ Unit 42. “From 2019-20, we noticed a dramatic 1,160% increase in malicious PDF files – from 411,800 malicious files to 5,224,056,” the researchers write. The most common form of PDF phishing lures use an image of a fake CAPTCHA to trick victims into clicking the “Continue” button, which leads to a malicious site. Another variant uses an image that purports to be a coupon, and tells victims to click the image in order to get 50% off on a product.
According to Hiscox, the average organization now devotes 21% of its IT budget to cybersecurity – a jump of 63% from around 13% of IT budget in 2020. According to the data, here's why: The percentage of organizations experiencing a cyberattack rose from 38% to 43%, of those experiencing an attack, 73% of them experienced more than one attack in the last 12 months and only 9% of attacked orgs say they were able to defend the attack with no impact to operations.
Researchers at Armorblox have spotted a credential phishing campaign that’s impersonating encrypted communications from Zix. The emails contain a link to download an HTML attachment. “This email is titled ‘Secure Zix message’, includes a header in the email body reiterating the email title, and claims that the victim has received a secure message from Zix, which is a security technology company that provides email encryption and email data loss prevention services,” the researchers write. “The email invites the victim to click on the ‘Message’ button to view the secure message.”
Cybercriminals are using QuickBooks’ popularity to send business email compromise (BEC) scams. The emails appear as if they are coming from a legitimate vendor using QuickBooks, but if the potential victim takes the bait, the invoice they pay will be to the scammer. Worse, the payment request can require that the payee use ACH (automated clearing house) method, which requires the payee to input their bank account details. So, if the victim falls for the scam, the criminal now has their bank account information.
One of the world’s most popular password managers, LastPass, recently had a bad data breach. They disclosed that although user’s plaintext passwords were not accessed, what the hackers did get included the following information: website URLs for the user’s stored passwords, end-user names, billing addresses, email addresses, telephone numbers, company names and IP addresses from which customers were accessing the LastPass service.
An unusual phishing technique has recently surfaced according to Avanan, a Check Point Software company. Phishing emails claim to be from DocuSign and hide malicious content inside a blank image within an HTML attachment. If the document is opened, the blank image attack begins. The attachment includes an SVG image encoded with Base64 containing Javascript that redirects to the malicious link. An Avanan Cybersecurity Researcher/Analyst points out that this amounts to a new variation of existing attack methods. “Hackers can target practically anyone with this technique. Like most attacks, the idea is to use it to get something from the end-user. Any user with access to credentials or money is a viable target. HTML attachments aren't new, nor are using Base64 trickery. What is new and unique is using an empty image with active content inside--a javascript image--which redirects to a malicious URL. It's essentially using a dangerous image, with active content inside that traditional services like VirusTotal don't detect.”
A year-long phishing campaign has been uncovered that impersonates 100+ popular clothing, footwear, and apparel brands using at least 10 fake domains impersonating each brand. According to internet security monitoring vendor Bolster, the 13-month long campaign used over 3000 live domains to impersonate over 100 well-known brands such as Nike, Guess, Fossil, Tommy Hilfiger, Skechers, and many more. Some of the domains have even existed long enough to be displayed at the top of natural search results.
Scammers are taking advantage of the popularity of the Barbie movie, according to researchers at McAfee. “In the last 3 weeks, we’ve seen 100 new instances of malware that have Barbie-related filenames,” the researchers write. “Once again, this shows how attackers have latched onto the movie’s hype, hoping the people will click the malicious files because the Barbie name is trending."
Find out what percentage of your employees are Phish-prone™ with your free phishing security test. Plus, see how you stack up against your peers with the new phishing Industry Benchmarks!
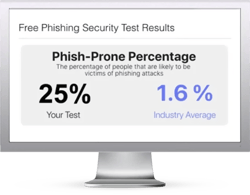
Here's how it works:
The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
There are a number of different techniques used to obtain personal information from users. As technology becomes more advanced, the cybercriminals' techniques being used are also more advanced.
To prevent Internet phishing, users should have knowledge of how cybercriminals do this and they should also be aware of anti-phishing techniques to protect themselves from becoming victims.

Think of spear phishing as professional phishing. Classic phishing campaigns send mass emails to as many people as possible, but spear phishing is much more targeted. The hacker has either a certain individual(s) or organization they want to compromise and are after more valuable info than credit card data. They do research on the target in order to make the attack more personalized and increase their chances of success.

In session hijacking, the phisher exploits the web session control mechanism to steal information from the user. In a simple session hacking procedure known as session sniffing, the phisher can use a sniffer to intercept relevant information so that he or she can access the Web server illegally.

Using the most common phishing technique, the same email is sent to millions of users with a request to fill in personal details. These details will be used by the phishers for their illegal activities. Most of the messages have an urgent note which requires the user to enter credentials to update account information, change details, or verify accounts. Sometimes, they may be asked to fill out a form to access a new service through a link which is provided in the email.

Content injection is the technique where the phisher changes a part of the content on the page of a reliable website. This is done to mislead the user to go to a page outside the legitimate website where the user is then asked to enter personal information.

Web based delivery is one of the most sophisticated phishing techniques. Also known as “man-in-the-middle,” the hacker is located in between the original website and the phishing system. The phisher traces details during a transaction between the legitimate website and the user. As the user continues to pass information, it is gathered by the phishers, without the user knowing about it.

Some phishing scams involve search engines where the user is directed to product sites which may offer low cost products or services. When the user tries to buy the product by entering the credit card details, it’s collected by the phishing site. There are many fake bank websites offering credit cards or loans to users at a low rate but they are actually phishing sites.

Link manipulation is the technique in which the phisher sends a link to a fake website. When the user clicks on the deceptive link, it opens up the phisher’s website instead of the website mentioned in the link. Hovering the mouse over the link to view the actual address stops users from falling for link manipulation.

In voice phishing, the phisher makes phone calls to the user and asks the user to dial a number. The purpose is to get personal information of the bank account through the phone. Vishing is mostly done with a fake caller ID.

Keyloggers refer to the malware used to identify inputs from the keyboard. The information is sent to the hackers who will decipher passwords and other types of information. To prevent key loggers from accessing personal information, secure websites provide options to use mouse clicks to make entries through the virtual keyboard.

Phishing conducted via Short Message Service (SMS), a telephone-based text messaging service. A smishing text, for example, attempts to entice a victim into revealing personal information via a link that leads to a phishing website.

A Trojan horse is a type of malware designed to mislead the user with an action that looks legitimate, but actually allows unauthorized access to the user account to collect credentials through the local machine. The acquired information is then transmitted to cybercriminals.

Phishing scams involving malware require it to be run on the user’s computer. The malware is usually attached to the email sent to the user by the phishers. Once you click on the link, the malware will start functioning. Sometimes, the malware may also be attached to downloadable files.

Malvertising is malicious advertising that contains active scripts designed to download malware or force unwanted content onto your computer. Exploits in Adobe PDF and Flash are the most common methods used in malvertisements.

Ransomware denies access to a device or files until a ransom has been paid. Ransomware for PC's is malware that gets installed on a user’s workstation using a social engineering attack where the user gets tricked in clicking on a link, opening an attachment, or clicking on malvertising.

Forged websites are built by hackers made to look exactly like legitimate websites. The goal of website forgery is to get users to enter information that could be used to defraud or launch further attacks against the victim.

One example is CEO fraud and similar attacks. The victim gets an email that looks like it's coming from the boss or a colleague, with the attacker asking for things like W-2 information or funds transfers. We have a free domain spoof test to see if your organization is vulnerable to this technique.

Hackers use devices like a pineapple - a tool used by hackers containing two radios to set up their own wi-fi network. They will use a popular name like AT&T Wi-Fi, which is pretty common in a lot of public places. If you're not paying attention and access the network controlled by hackers, they can intercept any info you may enter in your session like banking data.

Users can be manipulated into clicking questionable content for many different technical and social reasons. For example, a malicious attachment might at first glance look like an invoice related to your job. Hackers count on victims not thinking twice before infecting the network.
Every quarter, KnowBe4 reports on the top-clicked phishing emails by subject lines. we take a look at the top categories as well as subjects in the U.S. and Europe, the Middle East and Africa (EMEA). That data comes from millions of phishing tests our customers run per year. 'In The Wild' attacks are the most common email subjects we receive from our customers by employees clicking the Phish Alert Button on real phishing emails and allowing our team to analyze the results. We also track the top phishing attack vectors quarter to quarter. See the latest infographic below. Sharing this info with your users is a great way to keep them updated on the types of attacks their peers are currently falling for.
Over the past few years online service providers have been stepping up their security game by messaging customers when they detect unusual or worrisome activity on their users' accounts. Not surprisingly, threat actors are using this to their advantage. Many are designed poorly with bad grammar, etc. but others look legitimate enough for someone to click if they weren't paying close attention:
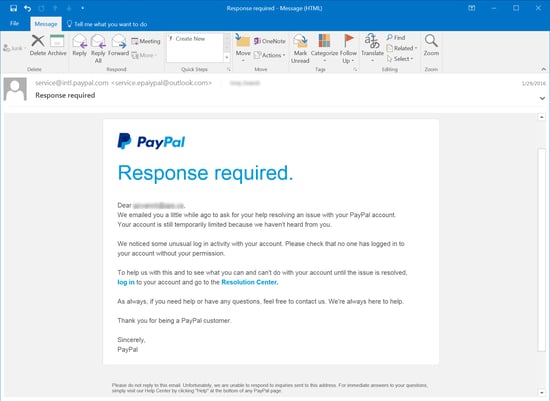
Consider this fake Paypal security notice warning potential marks of "unusual log in activity" on their accounts. Hovering over the links would be enough to stop you from ending up on a credentials stealing website. The first example is a fake Microsoft notice, almost identical in appearance to an actual notice from Microsoft concerning "Unusual sign-in activity". The second example email points users to a phony 1-800 number instead of kicking users to a credentials phish.
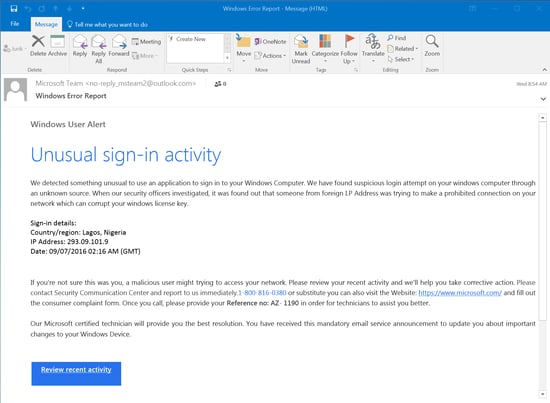
Malicious .HTML attachments aren't seen as often as .JS or .DOC file attachments, but they are desirable for a couple of reasons. First, there is a low chance of antivirus detection since .HTML files are not commonly associated with email-borne attacks. Second, .HTML attachments are commonly used by banks and other financial institutions so people are used to seeing them in their inboxes. Here are a few examples of credential phishes we've seen using this attack vector.
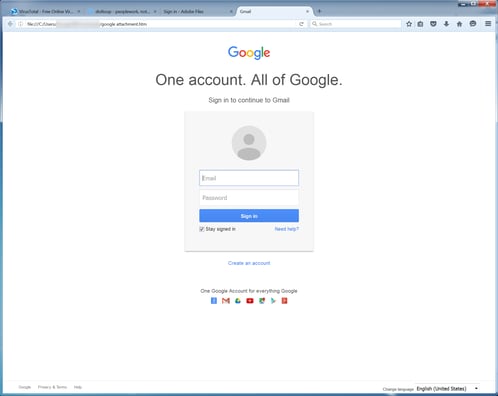
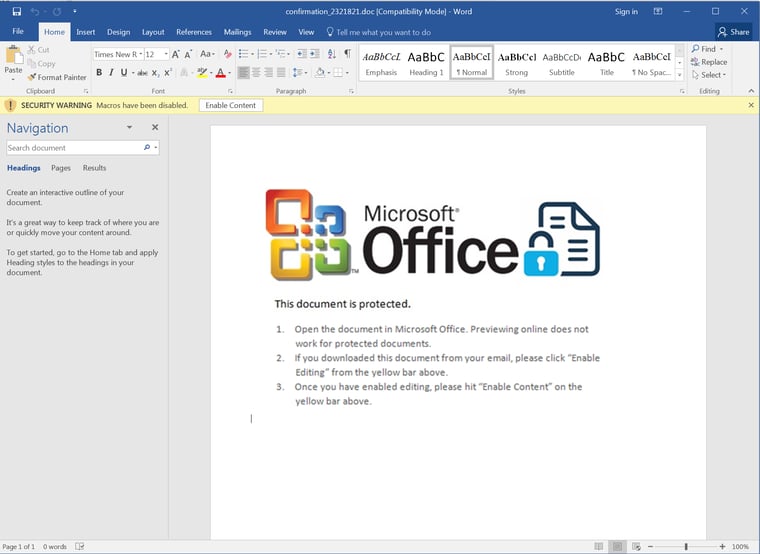
Malicious macros in phishing emails have become an increasingly common way of delivering ransomware in the past year. These documents too often get past antivirus programs with no problem. The phishing emails contain a sense of urgency for the recipient and as you can see in the below screenshot, the documents step users through the process. If users fail to enable the macros, the attack is unsuccessful.
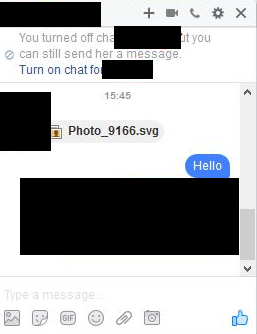
Several Facebook users received messages in their Messenger accounts from other users already familiar to them. The message consisted of a single .SVG (Scaleable Vector Graphic) image file which, notably, bypassed Facebook's file extensions filter. Users who clicked the file to open it were redirected to a spoofed Youtube page that prompted users to install two Chrome extensions allegedly needed to view the (non-existent) video on the page.
For most users, the two Chrome extensions were used to allow the malware a limited degree of self-propagation by exploiting the "browser's access to your Facebook account in order to secretly message all your Facebook friends with the same SVG image file."
On some users' PCs the embedded Javascript also downloaded and launched Nemucod, a trojan downloader with a long history of pulling down a wide variety of malicious payloads on compromised PCs. Users unlucky enough to encounter this version of the malicious script saw their PCs being taken hostage by Locky ransomware.
LinkedIn has been the focus of online scams and phishing attacks for a number of years now, primarily because of the wealth of data it offers on employees at corporations. Malicious actors mine that data to identify potential marks for business email compromise attacks, including wire transfer and W-2 social engineering scams, as well as a number of other creative ruses. Here are some examples we've seen through KnowBe4's Phish Alert Button:
In one case a user reported receiving a standard Wells Fargo credentials phish through LinkedIn's InMail: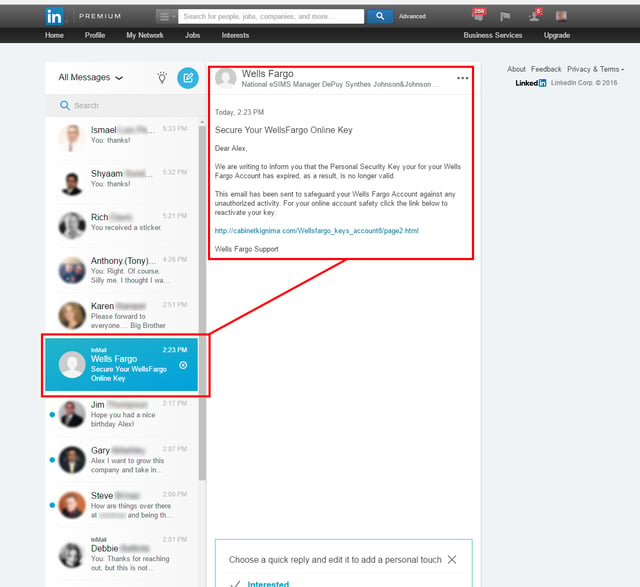
Note that this particular InMail appears to have originated from a fake Wells Fargo account. The supplied link leads to a fairly typical credentials phish (hosted on a malicious domain since taken down):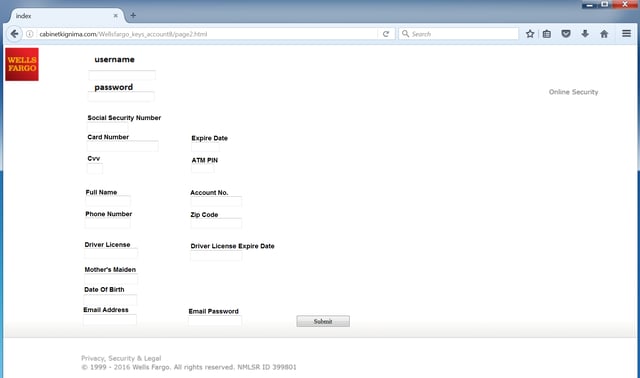
It looks like the cybercriminals set up a fake Wells Fargo profile in an attempt to appear more authentic.
Another similar phish was delivered to an email account outside of LinkedIn: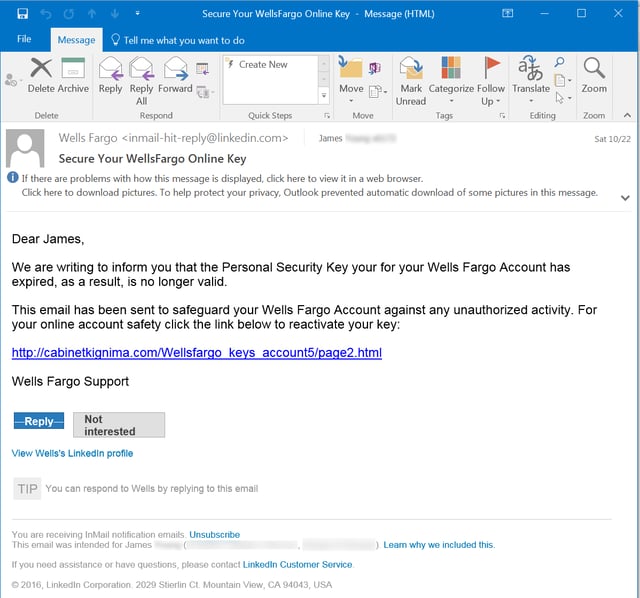
This email was delivered through LinkedIn, as did the URLs used for the several links included in the footer of this email ("Reply," "Not interested," "View Wells's LinkedIn profile"):
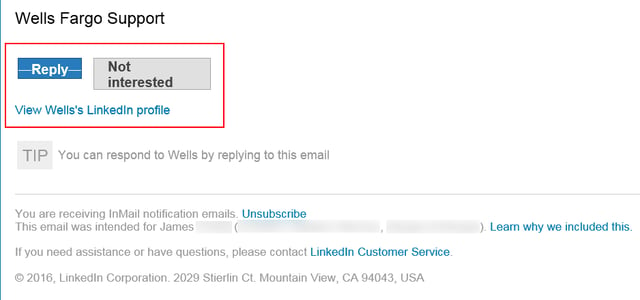
Those URLs were obviously auto-generated by LinkedIn itself when the malicious actors used LinkedIn's messaging features to generate this phish, which hit the external email account of the mark (as opposed to his InMail box, as was the case in the first phish discussed above).
Here's an example of a KnowBe4 customer being a target for CEO fraud. The employee initially responded, then remembered her training and instead reported the email using the Phish Alert Button, alerting her IT department to the fraud attempt.
When the employee failed to proceed with the wire transfer, she got another email from the cybercriminals, who probably thought it was payday:
Mobile phishing attacks have increased by 475% from 2019 to 2020, according to a recent report by Lookout. Attacks on mobile devices are nothing new, however they are gaining momentum as a corporate attack vector. Attackers now take advantage of SMS, as well as some of today’s most popular and highly used social media apps and messaging platforms, such as WhatsApp, Facebook Messenger, and Instagram, as a means of phishing. Security professionals who overlook these new routes of attack put their organizations at risk.
Here are just a few phishing related risks posed by mobile device use:
At a minimum, use this checklist to help mitigate the threat:
Next, implement a variety of best practices to address whatever security gaps may exist in the organization. For example:
Every organization should use historical and real-time threat intelligence to minimize the potential for infection. Real-time threat intelligence can provide a strong defense to protect against access to domains that have a poor reputation and, therefore, are likely to be used by cybercriminals for spearphishing, ransomware and other forms of attack. Threat intelligence can also be used proactively by security analysts and others to investigate recent attacks and discover previously unknown threat sources. Moreover, historical threat intelligence – such as a record of Whois data that includes information on who has owned domains in the past – can be useful in conducting cybercrime investigations.
Using both real-time and historical domain and IP-based threat intelligence is an important adjunct for any security infrastructure because it offers protection in several ways: There are good solutions available that can be deployed on-premises or in the cloud that can detect phishing attempts, ransomware and a variety of other threats.
Security patches are released for popular browsers all the time. They are released in response to the security loopholes that phishers and other hackers inevitably discover and exploit. If you typically ignore messages about updating your browsers, stop. The minute an update is available, download and install it.
High-quality firewalls act as buffers between you, your computer and outside intruders. You should use two different kinds: a desktop firewall and a network firewall. The first option is a type of software, and the second option is a type of hardware. When used together, they drastically reduce the odds of hackers and phishers infiltrating your computer or your network.
Every company struggles to answer an essential question—“How do I compare with other organizations who look like me?” To provide a nuanced and accurate answer, the 2024 Phishing By Industry Benchmarking Study analyzed a data set of over 11.9 million users across 55,675 organizations with over 54.1 million simulated phishing security tests across 19 different industries. All organizations were categorized by industry type and size. To calculate each organization’s Phish-prone Percentage, we measured the number of employees that clicked a simulated phishing email link or opened an infected attachment during a testing campaign using the KnowBe4 platform. The top industries at risk in this year's study in the small, medium and large organization categories are Healthcare & Pharmaceuticals (in both the small and large categories) and Hospitality in the medium category:

Results show a radical drop of careless clicking to just 18.9% within 90 days of initial training and simulated phishing and a steeper drop to 4.6% after 12 months of combined phishing and security awareness training.
Researchers anonymously tracked users by company size and industry at three points:
The 2024 Phishing By Industry Benchmarking Report compiles results from a new study by KnowBe4 and reveals at-risk users that are susceptible to phishing or social engineering attacks. The research also reveals radical drops in careless clicking after 90 days and 12 months of security awareness training.
Phishing and training your users as your last line of defense is one of the best ways to protect yourself from attacks. Here are the 4 basic steps to follow:
An additional 5 points to consider:
...and what we've found to be the 5 best practices to embrace:
Phishing your users is actually FUN! You can accomplish all of the above with our security awareness training program. If you need help getting started, whether you're a customer or not you can build your own customized Automated Security Awareness Program by answering 15-25 questions about your organization
With over 100 billion spam emails being sent daily, it's only a matter of time before you get hit. There are several ways you can and should report these:
