Tampa Bay, FL (March 18, 2016) – Ransomware is moving rapidly into the malware mainstream. One of the driving factors is the high dollar numbers racked up by the notorious Dridex banking Trojan gang muscling into ransomware with its new Locky strain. Locky was linked to the Dridex gang by IT security companies Palo Alto Networks and Proofpoint. The Russian Dridex group is the most prominent operating banking malware, taking over the lead from CryptoWall.
According to KnowBe4 CEO, Stu Sjouwerman, “Ransomware is seeing unprecedented growth with cyber-gangs competing for criminal market share. This competition spurred furious innovation in strategy and tactics, and we see ransomware taking the lead in criminal business models. It isn’t going to get easier. The only way around these tactics is to recognize the red flags and inoculate employees with effective security awareness training and simulated phishing tests.”
The Dridex Locky ransomware strain isn't more sophisticated than other latest generation crypto-ransom malware, but is rapidly spreading to victims’ systems. Forbes claims Locky is infecting approximately 90,000 systems per day (that’s over 1 per second) and it typically asks users for 0.5-1 Bitcoin (or $420 USD) to unlock their systems. Locky is disseminated through phishing emails containing Microsoft Word attachments. Each binary of Locky is reportedly uniquely hashed; consequently, signature-based detection by a traditional antivirus product is nearly impossible.
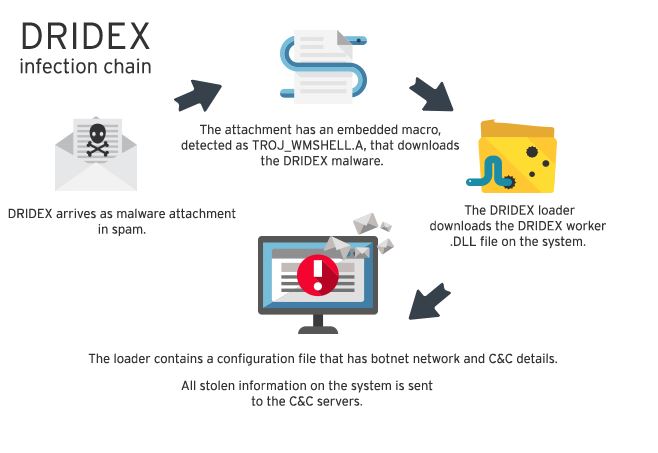
The Dridex gang is the 800-pound gorilla in banking Trojans. Apparently, it has seen the profit potential of ransomware, leveraging its extensive criminal infrastructure to get its Locky strain infecting as many machines as possible. Consequently, financial institutions are likely the next major sector to be actively targeted. The FBI stated that the threat from ransomware is expected to grow, according to a recent interview in the Wall Street Journal.
In the past few days, the Dridex botnet sent at least 4 million phishing emails with a zip file as the attachment, which contains a JavaScript file that downloads and installs Locky.
What to Do About It
- Block any and all emails with .zip extensions and/or macros at your email gateway level.
- Disable Adobe Flash Player, Java, and Silverlight if possible – these are used as attack vectors.
- Step all employees through effective security awareness training so they can recognize the red flags related to ransomware attacks.
- Print out this (https://cdn2.hubspot.net/hubfs/241394/Knowbe4-May2015-PDF/SocialEngineeringRedFlags.pdf) free job aid, laminate it, and hand it out to employees so they can pin it on their wall.
- Do a Phishing Security Test on your users to find out if they will click on something they shouldn't. For more information, or to sign up for a free test, visit https://info.knowbe4.com/phishing-security-test-16.
KnowBe4 also offers a crypto-ransom guarantee and will pay its customer’s ransom if the company gets hit with ransomware due to human error of an employee.
About Stu Sjouwerman and KnowBe4
Stu Sjouwerman (pronounced “shower-man”) is the founder and CEO of KnowBe4, Inc., which hosts the world’s most popular integrated Security Awareness Training and Simulated Phishing platform. A data security expert with more than 30 years in the IT industry, Sjouwerman was the co-founder of Inc. 500 company Sunbelt Software, a multiple award-winning, anti-malware software company that was acquired in 2010. Realizing that the human element of security was being seriously neglected, Sjouwerman decided to help organizations manage the problem of cybercrime social engineering tactics through new school security awareness training.
Thousands of organizations, in a variety of industries, including highly-regulated fields, such as healthcare, finance, energy, government, and insurance have mobilized their end users as a first line of defense using KnowBe4. Sjouwerman is the author of four books, with his latest being “Cyberheist: The Biggest Financial Threat Facing American Businesses.” For more information, visit www.knowbe4.com and follow on @KnowBe4 Twitter.