RanSim
Is your network effective against ransomware infections when employees fall for social engineering attacks?
"RanSim" software gives you a quick look at the effectiveness of your existing network protection.
It will test 24 ransomware infection scenarios and 1 cryptomining infection scenario and show you if a workstation is vulnerable.
How RanSim works:
- 100% harmless simulation of real ransomware and cryptomining infections
- Does not use any of your own files
- Tests 25 types of infection scenarios
- Just download the installer and run it
- Results in a few minutes!
NOTE: Created for Windows-based workstations running Windows 10+. RanSim does not alter any existing files on disk. As part of the software, RanSim does enumerate all files on the local disk(s). For the purposes of encryption, simulated data files are downloaded from the Internet.
I want my RanSim download
Ransomware Defined
Ransomware is defined as vicious malware that locks users out of their devices or blocks access to files until a sum of money or ransom is paid. Ransomware attacks cause downtime, data loss, possible intellectual property theft, and in certain industries an attack is considered a data breach.
Learn about more ransomware examples, mobile phishing, and how to prevent attacks on our Ultimate Resource to Ransomware.
Ransomware FAQs
STEP 1: Disconnect Everything - Unplug the infected computer(s) from network, and turn off any wireless functionality: Wi-Fi, Bluetooth, NFC.
STEP 2: Determine the Scope of the Infection, Check the Following for Signs of Encryption:
a. Mapped or shared drives
b. Mapped or shared folders from other computers
c. Network storage devices of any kind
d. External Hard Drives
e. USB storage devices of any kind (USB sticks, memory sticks, attached phones/cameras)
f. Cloud-based storage: DropBox, Google Drive, OneDrive etc.
STEP 3: Determine if data or credentials have been stolen - Check logs and DLP software for any and all signs of data leaks. Look for unexpected large archival files (e.g., zip, arc, etc.) containing confidential data that could have been used as staging files. Look for malware, tools, and scripts which could have been used to look for and copy data. One of the most accurate signs of ransomware data theft is a notice from the involved ransomware gang announcing that your data and/or credentials have been stolen.
STEP 4: Determine Ransomware Strain - What strain/type of ransomware? For example: Ryuk, Dharma, SamSam, etc.
STEP 5: Determine Response - Now that you know the scope of the damage as well as the strain of ransomware you are dealing with, you can make a more informed decision as to what your next action will be. There are many response types, here is a summary of potential responses:
Response 1: If Data or Credentials are Stolen 1. Determine if ransom should be paid to prevent data or credentials from being released by hackers. 2. If ransom is to be paid, you can skip steps #1 and #3 of Response 2 from recovery.
Response 2: If Ransom Is Not Paid and You Need to Restore Your Files From Backup 1. Locate your backups a. Ensure all files you need are there. b. Verify integrity of backups (i.e. media not reading or corrupted files). c. Check for Shadow Copies if possible (may not be an option on newer ransomware). d. Check for any previous versions of files that may be stored on cloud storage e.g. DropBox, Google Drive, OneDrive. 2. Remove the ransomware from your infected system. 3. Restore your files from backups. 4. Determine infection vector & handle.
Response 3: Try to Decrypt 1. Determine strain and version of the ransomware if possible 2. Locate a decryptor, there may not be one for newer strains. If successful, continue steps... 3. Attach any storage media that contains encrypted files (hard drives, USB sticks etc.) 4. Decrypt files 5. Determine the infection vector & handle.
Response 4: Do Nothing (Lose Files) 1. Remove the ransomware 2. Backup your encrypted files for possible future decryption (optional).
Response 5: Negotiate and/or Pay the Ransom 1. If possible, you may attempt to negotiate a lower ransom and/or longer payment period. 2. Determine acceptable payment methods for the strain of ransomware: Bitcoin, Cash Card etc. 3. Obtain payment, likely Bitcoin: a. Locate an exchange you wish to purchase a Bitcoin through (time is of the essence). b. Set up account/wallet and purchase the Bitcoin. 4. Re-connect your encrypted computer to the internet. 5. Install the TOR browser (optional). 6. Determine the Bitcoin payment address. This is either located in the ransomware screen or on a TOR site that has been set up for this specific ransom case. 7. Pay the ransom: Transfer the Bitcoin to the ransom wallet. 8. Ensure all devices that have encrypted files are connected to your computer. 9. File decryption should begin within 24 hours, but often within just a few hours. 10. Determine infection vector and handle.
STEP 6: Protecting Yourself in the Future - Develop and implement a Ransomware prevention checklist, specific to your organization, to prevent future attacks.
It’s a given that ransomware is here to stay for the foreseeable future. It’s not new, so organizations should be pretty well-versed in how to stave an attack, as well as how to remediate one should it successfully encrypt the organization’s data and/or systems. However, attacks have changed in recent years so these are the best prevention steps to take:
- Basic Cybersecurity Hygiene. Improving basic cybersecurity hygiene is the most important defense against any type of attack, including ransomware. Cybersecurity hygiene can mean a lot of different things, but a good place to start is by making sure you have strong vulnerability management practices in place and that all devices have the latest security patches. Other basic security precautions can include running up-to-date antivirus software, restricting access to systems that can't be made compliant and other actions you would already take for regulatory compliance.
- Penetration Testing. Once basic cybersecurity hygiene is covered, a further step may be engaging pen testers to further ensure that anything Internet-facing in your organization is protected. By finding what means or mechanisms attackers could hack or brute-force an attack to gain access to applications or internal systems by bypassing other protections such as firewalls, you can take action to fix those areas before bad actors find them.
- Board Discussions. Cybersecurity is increasingly becoming a board of directors-level issue. That's because an attack can have a significant impact on an organization's revenue, brand, reputation, and ongoing operations. Because of that, it's worth having a specific board-level conversation about ransomware to ensure they understand the specific risks it could pose to the business, and that there is budget made available to prevent or limit the damage of an attack. That discussion will prove critical if the company wants to implement added protections, such as improved cyber hygiene, or put in place automated reactive technologies to limit the spread of an attack.
- Tailored Training. There is one vulnerability that has proven effective again and again as an entry point for attack: people. You can buy all the latest and greatest cybersecurity technology, but if you aren't training your employees, then you're leaving yourself vulnerable. Training to prevent ransomware starts by teaching employees to recognize phishing attacks and what to do if they suspect one. This is important because — even though many users have gotten better — phishing and social engineering remain two of the most effective ways for an attacker to breach your organization. Teaching users to validate URLs or avoid clicking on links or attachments altogether can go a long way toward protecting against all types of attacks.
In addition to preventing an attack, security leaders can also think about adding specific training for ransomware response. It's pretty easy for an employee to know when they've been hit with ransomware — their work screen may go away and they may get a pop-up directing you to a URL to pay the ransomware (likely in bitcoin). Training your users in what steps they can take in response or giving them an emergency point of contact on the security team can make them feel more in control in the panic of an attack. - Limit the Scope of an Attack. Ransomware protection should include not only preventing an attack but also taking steps to minimize the damage of a successful one. That starts with having tools in place, such as SIEM systems that can identify the behavior patterns and heuristics of an attack and begin to automatically isolate and remediate those systems when indicators are flagged. It also means embracing tools such as network segmentation that can prevent the lateral movement of an attack across the network
Email Vector - By far the most common scenario involves an email attachment disguised as an innocuous file. Many times hackers will send a file with multiple extensions to try to hide the true type of file you are receiving. If a user receives a phishing email with an attachment or even a link to a software download, and they install or open that attachment without verifying its authenticity and the sender’s intention, this can lead directly to a ransomware infection. This is the most common way ransomware is installed on a user’s machine.
Drive-by-Download - Increasingly, infections happen through drive-by downloads, where visiting a compromised website with an old browser or software plug-in or an unpatched third party application can infect a machine. The compromised website runs an exploit kit (EK) which checks for known vulnerabilities. Often, a hacker will discover a bug in a piece of software that can be exploited to allow the execution of malicious code. Once discovered, these are usually quickly caught and patched by the software vendor, but there is always a period of time where the software user is vulnerable.
Free Software Vector - Another common way to infect a user’s machine is to offer a free version of a piece of software. This can come in many flavors such as “cracked” versions of expensive games or software, free games, game “mods”, adult content, screensavers or bogus software advertised as a way to cheat in online games or get around a website’s paywall. By preying on the user in this way, the hackers can bypass any firewall or email filter. After all, the user downloaded the file directly themselves! An example is a ransomware attack which exploited the popularity of the game Minecraft by offering a “mod” to players of Minecraft. When they installed it, the software also installed a sleeper version of ransomware that activated weeks later.
One method cybercriminals will use to install malicious software on a machine is to exploit one of these unpatched vulnerabilities. Examples of exploits can range from vulnerabilities in an unpatched version of Adobe Flash, a bug in Java or an old web browser all the way to an unpatched, outdated operating system.
Remote Desktop Protocol (RDP) - Internet-exposed Remote Desktop Protocol (RDP) sessions are another very common means of infecting networks. RDP sessions are used to remotely log in to Windows computers and allow the user to control that computer as if they were sitting in front of it. The technology typically uses port 3389 to communicate, and many organizations allow traffic from the internet through their firewall, so people can remotely access the computer. Hackers have become increasingly skilled at attacking these exposed computers and using them to spread malware within a network. RDP is exploited either due to an unpatched vulnerability or due to password guessing because the victims chose very weak passwords and/or did not enable account lockout protections.
- Click Launch to launch RanSim or double-click the RanSim icon on your desktop.
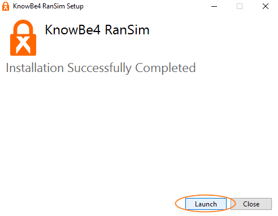
- Click the Check Now button to start the RanSim software. After clicking, RanSim will run 21 separate infection scenarios. It will also run two "false positive" scenarios, which your antivirus should allow to run.


- After the scans are completed, a results screen will show if your system is vulnerable or not, based on each of the 21 scenarios and the two false-positive scenarios. There will also be a count of how many files would have been vulnerable if an actual ransomware attack had occurred.

If you'd like, you can perform additional checks by clicking the Check Now button again. After running your first analysis, you can optionally add your own test files to the test files folder. Those files will be used in any additional checks you perform with RanSim, to see if they are vulnerable to encryption by a ransomware attack.
See the full RanSim Product Manual for more details.
Once RanSim has finished running all of the test scenarios, you can download a CSV file of the information you found after launching RanSim. This CSV can be used to compare how your files hold up against the various ransomware attacks. You can find the download link in the top right corner of the Results page.
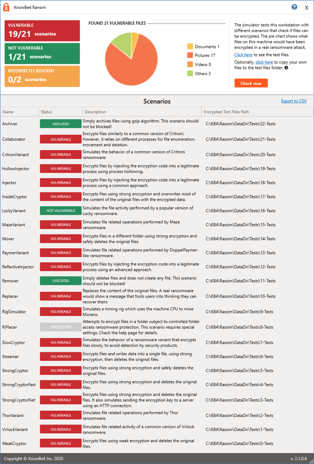
These results can be used to secure any documents and files that failed any of the infection scenarios. Implementing security awareness training to prepare your users on what they can do to identify a phishing attack will reduce the risk of your organization falling victim to a ransomware attack.
See the full RanSim Product Manual for more details.
Yes! The emergence of new strains has slowed down, but ransomware has gone nuclear and is getting much more sophisticated. In the early days, hackers mostly targeted consumers, and it would encrypt immediately upon executing. Later on, ransomware gangs realized they would make a lot more money targeting businesses. At first they would spread like a worm through organizations, collecting credentials and encrypting files along the way. Threat actors are now a lot more intelligent in their approach. Once they've gotten in, the malware 'dials home' so that the hacker can do a full analysis on which data is most valuable to their victim, how much they can realistically ask for, and what can they encrypt that will get them a payday sooner.
Most of the ransomware gangs are now exfiltrating your most valuable data and threaten to expose it on publicly available websites as an additional extortion method. Some of these criminals make you pay twice, once for the decryption key, and again to delete the data they have stolen. In the U.S. alone, a single cybersecurity insurance consortium said they are paying $1M per day in ransomware payouts to these criminal gangs.
That figure doesn't include recovery and downtime costs, which can far exceed the cost of the ransom. By now, there are tens of thousands of ransomware victims, including school districts, police departments, and entire cities. It is important to understand that it is not just large organizations that are targeted, small and medium organizations are also at risk.
Cybercriminals constantly use social engineering and update their ransomware themes to stay current. Some themes include the FBI variant, the Internal Revenue Service, and even sadly, now COVID-19 pandemic-themed ransomware. In addition to updating themes, cybercriminals are also developing creative new ways to spread the ransomware. These include offering Ransomware-as-a-Service (RaaS) strains such as “Dot” or “Philadelphia”, where they offer your files back for free if you infect two other organizations. There are even marketing videos on YouTube for some ransomware strains.