Samas ransomware, also known as SamSam, Kazi, or RDN/Ransom is an aggressive hybrid attack that attempts to infect all machines on an organization's network. It initially targeted vulnerable JBOSS applications allowing the hackers access to infect the network. Here is a flowchart of how it works:
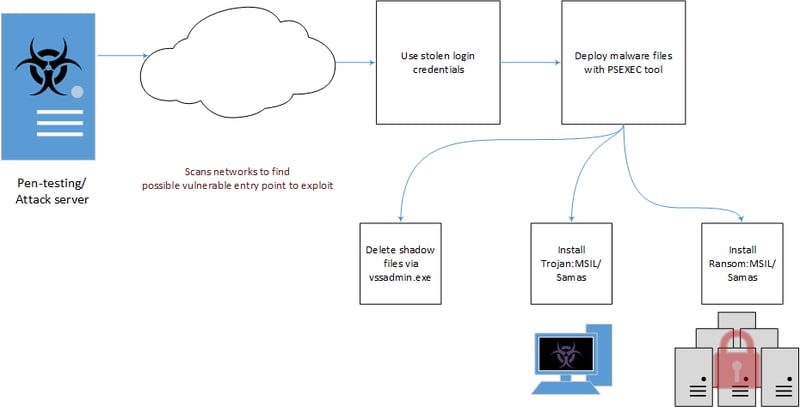
Samas starts with a pen-test/attack server that scans for network vulnerabilities. It incorporates Java-based vulnerabilities and other information stealing malware to collect login credentials, which are then used to deploy the ransomware and its components through a third party tool.
Unlike usual attack vectors like phishing emails or drive-by downloads, the cybercriminals gained persistent access to the victim’s network through vulnerability exploitation and spread their access to any connected systems available. On each system several tools were used to find, encrypt, and delete the original files and any connected backups. One unlucky victim even had their Veeam backups get totally wiped out.
The tools used were some Microsoft Sysinternals utilities and parts of open-source projects. By using different free tools and scripts that are available for anyone to use, the adversaries did their best to avoid detection. This is a very targeted ransomware attack, different from most we've seen that spread wherever possible.
After file encryption is complete, a ransom note appears demanding payment in Bitcoins to get the files back. At this time there is no known free decryption available for Samas ransomware. However, microsoft does offer some mitigation and prevention tips for this strain like disabling the loading of macros in Office programs through Group Policy settings like we suggested.
