Virlock ransomware was first seen in 2014 but in September of 2016 was found to be capable of spreading across networks via cloud storage and collaboration apps. This strain uses a variety of threat techniques.
So how does Virlock work? Unlike most ransomware, this strain not only encrypts selected files but also converts them into a polymorphic file infector just like a virus. In addition to files we are used to seeing being targeted, Virlock also infects binary files. This means Virlock weaponizes every single file it infects, any user that opens an infected file will also infect and encrypt all of that user's files.
User A and User B are collaborating through the cloud storage app Box, using a folder called "Important". Both users have some of the files within the folder synced to their own machine.
User A gets infected with Virlock ransomware on their machine, encrypting all their files, including the files which are synced on Box. So, Virlock also spreads to the cloud folder and infects the files stored there, which in turn get synced to User B's machine.
User B then clicks on any of the files in the shared folder on their box, the infected Virlock file is executed and the rest of the files on the machine of User B become infected and in their turn becoming Virlock file infectors just like a virus.
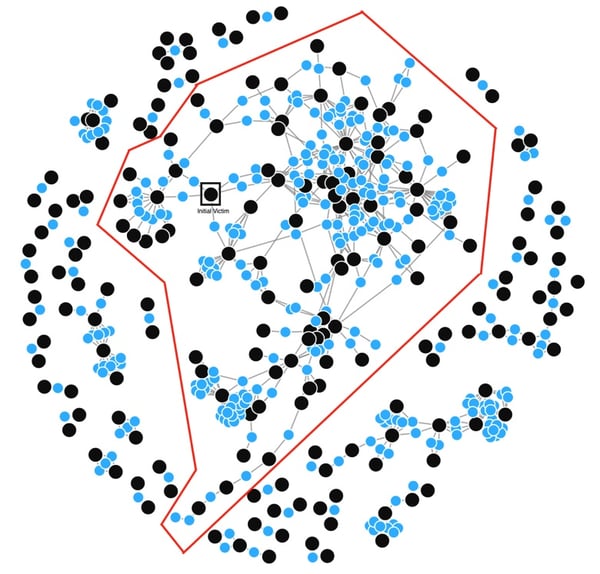
This example is by no means limited to just User A and User B. Because each infected file becomes an infector, the infection will spread to all users that are collaborating within the same cloud environment. Consider the User-File collaboration graph below of a typical enterprise with users (in black dots) and the files (in blue dots). All the users within the red boundary could get infected with Virlock ransomware within minutes.
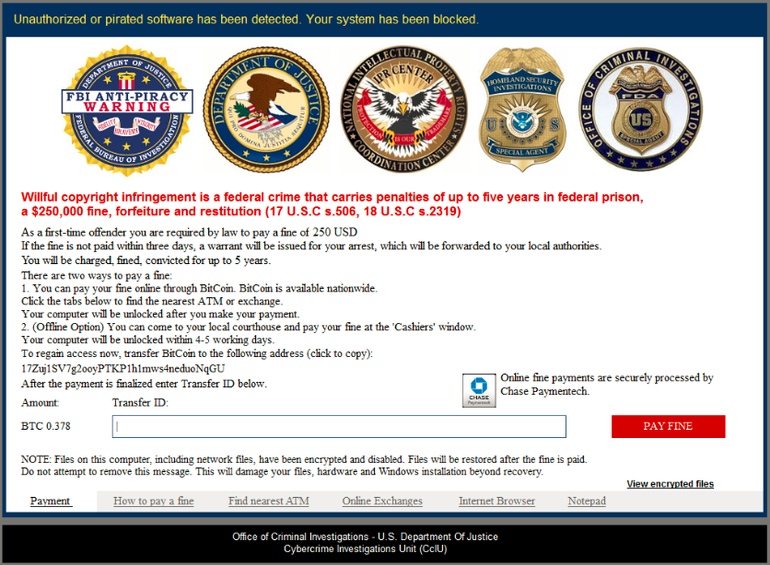
Virlock asks the victim for a payment in Bitcoin to decrypt their files, however, unlike other ransomware strains, Virlock appears to be an anti-piracy warning from the FBI.
The ransom note claims pirated software has been found on the infected machine and threatens the victims with prison and a $250,000 fine if they don't pay a $250 'first-time offender' fine. This is an old social engineering tactic that has been used by cybercriminals for years in an attempt to scare victims into just paying the ransom quickly.
Threat actors count on ransom payments to continue upgrading their infrastructure. The problem with Virlock is that say a victim pays the ransom, how can they be sure every file is completely restored? If just one file is left infected the entire network is still vulnerable and how many organizations would pay ransom twice to recover from the same infection? Our guess is not many.
The spread of an infection like Virlock counts on users not paying attention. Yet another reason to make sure all of your users have proper security awareness training!
