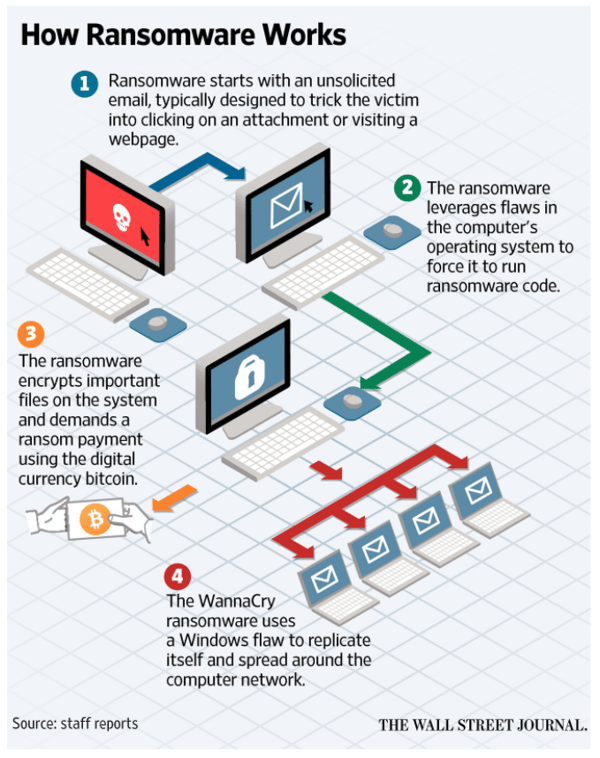
WannaCry ransomware appeared in May of 2017, starting with a massive attack on vulnerable SMB services, railways, telcos, universities, the UK's NHS, and so on. The ransomworm strain infected over 300,000 computers in over 150 countries, making the criminals $90,000 which is really not that much compared to the amount of infections. WannaCry was to date the biggest ransomware outbreak in history and really caused the world to take notice of ransomware.
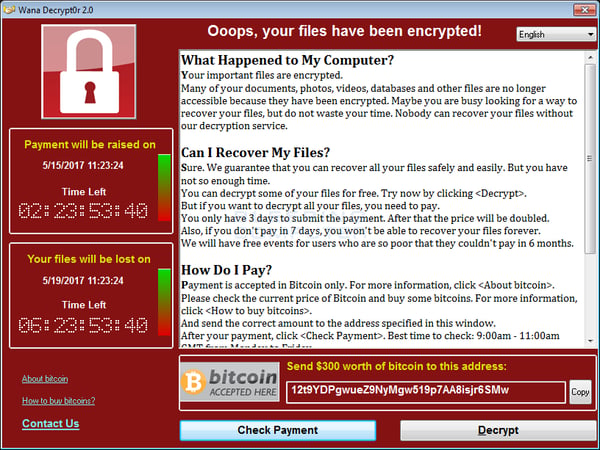
The strain is called "Wana Decryptor" which asks $300 from victims to decrypt their computers. This monster has infected hundreds of thousands of systems in more than 150 countries. Monday morning when people get back to work, these numbers will only go up. Check out an early animated map created by the NYTimes.
The IT systems of around 40 National Health System hospitals across the UK were affected by this attack. Non-emergency operations had to be suspended and ambulances were diverted as a result of the infection. Cybersecurity experts have long used the phrase "where bits and bytes meet flesh and blood," which signifies a cyberattack in which someone is physically harmed.
A North Korean hacking group is suspected to be behind the worldwide WannaCry attack that caused 1 billion dollars in damage, targeting mainly un-patched Windows 7 machines. Symantec and Kaspersky malware labs are investigating technical evidence that possibly suggests the North’s involvement, claiming they found some code in an earlier version of the WCry ransomware that had also been used in programs deployed by the Lazarus Group, which is reportedly run by the Norks. The below graph from Symantec shows how quickly WannaCry spread:
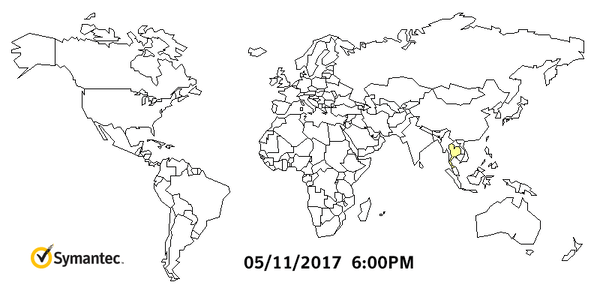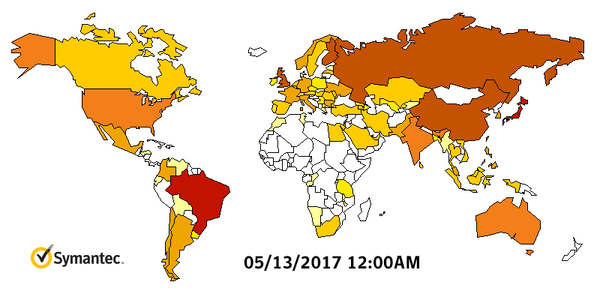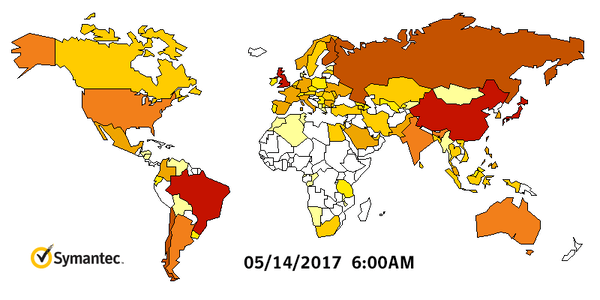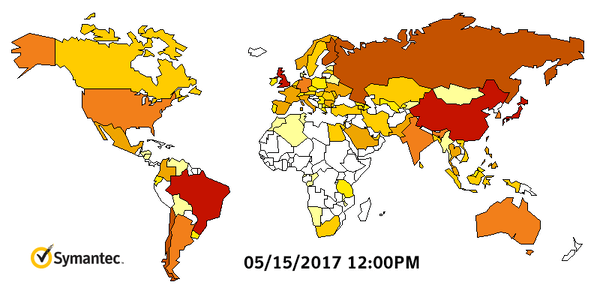
This is spy territory and the best way to approach attribution is to deal in probabilities and intelligence estimates that are never 100%, unless you can hack into the machines of the actual coders behind an attack, which is very unlikely. That said, there's a 70–80% chance that WannaCry originated in North Korea based on forensic evidence we've seen so far.
The ransom starts at $300 if you pay within 6 hours, then it doubles to $600 for up to 3 days later. The ransomware threatens to delete the files completely If you don't pay within a week, and includes an ominous countdown timer to your files being deleted. Note the social engineering aspect here too: a sense of urgency is created to prompt people into action. A sense of hope is granted by virtue of the ability to decrypt a sample selection of the files.
Security experts initially thought the infection vector was a mass phishing campaign sending its potential victims fake invoices. However, SophosLabs VP Simon Reed said this looks like a worm from start to finish: "There were no outlook.exe files anywhere, nothing but a compromised Windows SMB driver as the starting point. So far, we haven’t found anything but evidence of a network worm."
So this outbreak was a throwback to those of the early 2000s. But instead of just noise and network downtime, a much more damaging payload of ransomware ground many organizations to a halt.
WannaCry uses what was originally NSA 0-day ETERNALBLUE and DOUBLEPULSAR exploits which were made public earlier this year by a group calling itself the ShadowBrokers. There are recent patches available but many have not applied them yet.
Edward Snowden pointed the finger at the NSA, implying the agency was responsible for exploiting a weakness in Windows.It is unclear how the ShadowBrokers may have gotten their hands on these NSA tools - conspiracy theories range from a contractor leak to a Russian counter-espionage trying to hint American intelligence should back off.
One of the easiest ways to monitor what is happening on your network is to setup a SPAN\Mirror port or use a network TAP. This will give you access to flows and packet payloads so you can see who is connecting to what and if there is anything suspicious moving around. Check out this blog post if you use Cisco switches, it explains how you can monitor multiple network segments without the need to remember what is connected to what switch port. If you don't use Cisco switches there is an excellent resource on the Wireshark wiki site which looks at how to setup monitoring on other switches.
There is one caveat though, this infection moves out like lightning from patient zero, and all vulnerable machines are literally locked in less than two minutes so monitoring alone would not be enough to be stop this monster Here is a video showing a machine on the left infected with MS17-010 worm, spreading WCry ransomware to machine on the right in real time.
This ransomware strain cannot be decrypted with free tools. Research shows the encryption is done with RSA-2048 encryption. That means that decryption will be next to impossible, unless the coders have made a mistake that has not been found yet.
Your best bet is to recover from backups, and if your backup failed or does not exist, try a program like Shadow Explorer to see if the ransomware did not properly delete your Shadow Volume Copies. If a user did not click Yes at the UAC prompt, then there is a chance those are still available to start the recovery. Here is How to recover files and folders using Shadow Volume Copies. As a last resort and all backups have failed, you could decide to pay and get the files decrypted. It appears to work.
It's possible but difficult. Some bitcoin has reportedly been paid into hackers' accounts and investigators can track the money and see where the bitcoin ends up. "Despite what people tend to think, it's highly traceable," Clifford Neuman, who directs the University of Southern California's Center for Computer Systems Security, told the Washington Post.
However, hackers are still able to hide and launder the bitcoins in many different ways. Investigators will also examine the code itself as hackers often leave identifiable traces of their work. You can watch as some of these wallets are receiving money in real time. There is an international manhunt underway.